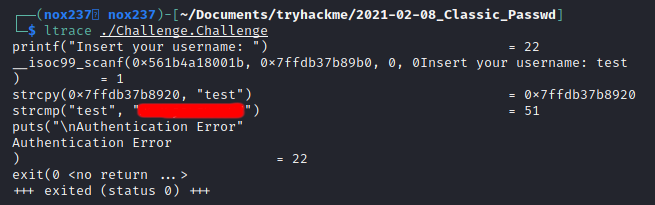
In this room, the file was using strcmp function which contained the string that can be used to bypass the authentication. To solve the challenge, it can be done using reverse engineering tools like gdb or ltrace.
Walkthrough
From the download file, I found that it was “ELF 64-bit LSB pie executable” binary that I can run on linux environment. But it need a username to get the answer, otherwise it will print “Authentication Error” message.
Using gdb on linux environment, I execute disassemble function on main where I found the function will call vuln function.
1
2
3
4
5
6
7
8
9
10
11
Dump of assembler code for function main:
0x00005555555552f6 <+0>: push rbp
0x00005555555552f7 <+1>: mov rbp,rsp
0x00005555555552fa <+4>: mov eax,0x0
0x00005555555552ff <+9>: call 0x555555555185 <vuln>
0x0000555555555304 <+14>: mov eax,0x0
0x0000555555555309 <+19>: call 0x555555555289 <gfl>
0x000055555555530e <+24>: mov eax,0x0
0x0000555555555313 <+29>: pop rbp
0x0000555555555314 <+30>: ret
End of assembler dump.
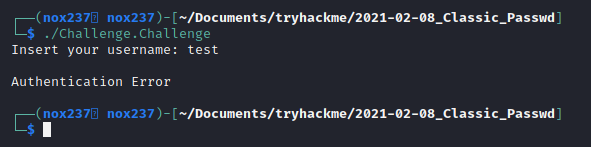
Inside the function, I found that it will compare our input to a string using strcmp function that was located on 0x000055555555525a address (this address was on my machine, yours address might be different).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
Dump of assembler code for function vuln:
0x0000555555555185 <+0>: push rbp
0x0000555555555186 <+1>: mov rbp,rsp
0x0000555555555189 <+4>: sub rsp,0x2c0
0x0000555555555190 <+11>: movabs rax,0x207962206564614d
# There is other instructions that I do not put inside this
0x0000555555555228 <+163>: call 0x555555555070 <__isoc99_scanf@plt>
0x000055555555522d <+168>: lea rdx,[rbp-0x230]
0x0000555555555234 <+175>: lea rax,[rbp-0x2c0]
0x000055555555523b <+182>: mov rsi,rdx
0x000055555555523e <+185>: mov rdi,rax
0x0000555555555241 <+188>: call 0x555555555030 <strcpy@plt>
0x0000555555555246 <+193>: lea rdx,[rbp-0x23e]
0x000055555555524d <+200>: lea rax,[rbp-0x2c0]
0x0000555555555254 <+207>: mov rsi,rdx
0x0000555555555257 <+210>: mov rdi,rax
0x000055555555525a <+213>: call 0x555555555060 <strcmp@plt>
0x000055555555525f <+218>: test eax,eax
0x0000555555555261 <+220>: jne 0x555555555271 <vuln+236>
0x0000555555555263 <+222>: lea rdi,[rip+0xdb4]
0x000055555555526a <+229>: call 0x555555555040 <puts@plt>
0x000055555555526f <+234>: jmp 0x555555555287 <vuln+258>
0x0000555555555271 <+236>: lea rdi,[rip+0xdaf]
0x0000555555555278 <+243>: call 0x555555555040 <puts@plt>
0x000055555555527d <+248>: mov edi,0x0
0x0000555555555282 <+253>: call 0x555555555080 <exit@plt>
0x0000555555555287 <+258>: leave
0x0000555555555288 <+259>: ret
I set a breakpoint on the strcmp function address using breakpoint 0x000055555555525a and then I print the value of the function parameter using x/s on each rax and rdx where I find the value of inputted string and the string that used to be compared with.
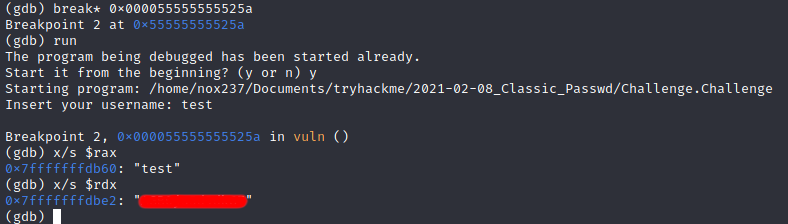
The username that found on the debugger can be used to gain the flag for this challenge where we can supply the string as input.
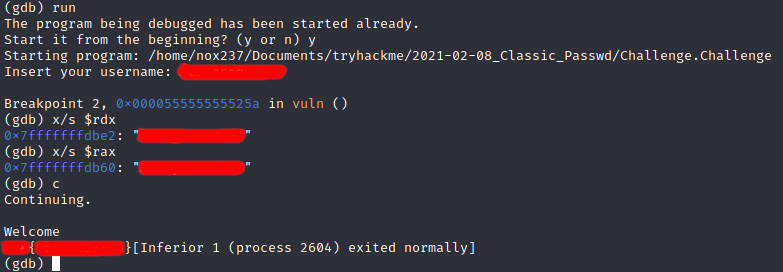
Other methods
I found that using ltrace, we can trace the library that was used in the binary which is strcmp function and also print the string that was used to compare.