Microsooft
Description
We have to use Microsoft Word at the office!? Oof…
Download the file below.
Solution
From my previous storage, a .docx file can be unzip because it is a single, compressed file:
1
unzip microsooft.docx
After we extract the .docx file, we can use grep command to search for our flag:
1
grep -oE 'flag{.*}' -r
From that command, the results will be our flag”
1
2
src/gfxdata_extract/oof.txt:flag{oof_is_right_why_gfxdata_though}
src/oof.txt:flag{oof_is_right_why_gfxdata_though}
Flag
Flag : flag{oof_is_right_why_gfxdata_though}
Alkatraz
Description
We are so restricted here in Alkatraz. Can you help us break out?
Connect here: nc jh2i.com 50024
Solution
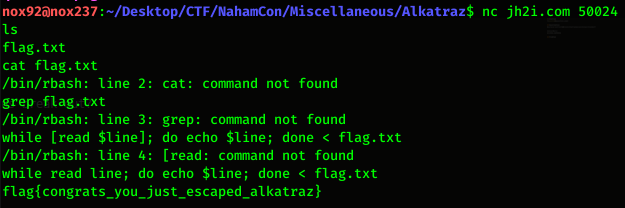
Notes: From the netcat, we will get a prompt where we can run our command in the server. But on the server, we cannot run command like grep or cat because the comnand was not there. To get the flag, i use linux command like this:
1
while read line; do echo $line; done < flag.txt
Flag
Flag : flag{congrats_you_just_escaped_alkatraz}
Fake File
Description
Wait… where is the flag?
Connect here: nc jh2i.com 50026
Problem
After accessing the server with netcat, we will found this file:
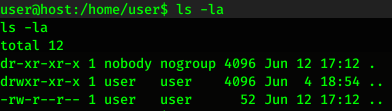
As you can see from the picture above, the file name is ‘..’, so to see the flag we can run this command:
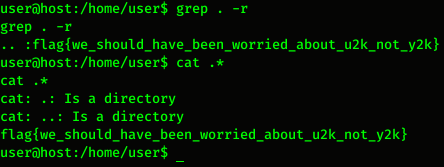
Flag
Flag : flag{we_should_have_been_worried_about_u2k_not_y2k}
Simple App

Description
Here’s a simple Android app. Can you get the flag?
Download the file below.
Solution
First, i run command strings simple-app.apk. Using the strings command, we will not get flag. So the second method that i use is to decompile the apk file using apktool:
1
apktool d simple-app.apk
After decompile it, i run this command and we will get the flag:
1
grep -oE 'flag{.*}' -r
1
smali/com/example/simple_app/MainActivity.smali:flag{3asY_4ndr0id_r3vers1ng}
Flag
Flag : flag{3asY_4ndr0id_r3vers1ng}
Candroid
Description
I think I can, I think I can!
Download the file below.
Solution
To solve this challenge, i run this command and we will get the flag:
1
strings candroid.apk | grep -oE "flag{.*}"
Flag
Flag : flag{4ndr0id_1s_3asy}
Mr. Robot
Description
Elliot needs your help. You know what to do.
Connect here: http://jh2i.com:50032
Problem
When visiting the challenge, we will get this website interface:
The step that i try is to download poster.jpg and try to strings the command:
1
strings poster.jpg | grep -oE "flag{.*}"
But the flag was not in the picture. After looking on the challenge name, i think that the challenge maybe refer to robots.txt. Then when we run command like curl, we will get the flag.
1
curl "http://jh2i.com:50032/robots.txt"
Flag
Flag : flag{welcome_to_robots.txt}
UGGC
Description
Become the admin!
Connect here: http://jh2i.com:50018
Problem
After inspecting on the challenge website, i try to do simple SQL injection like ‘ OR 1=1 but it will not login as admin. When testing the challenge, i will become the user that i input and if we look at the cookies we can change our privilege to admin.
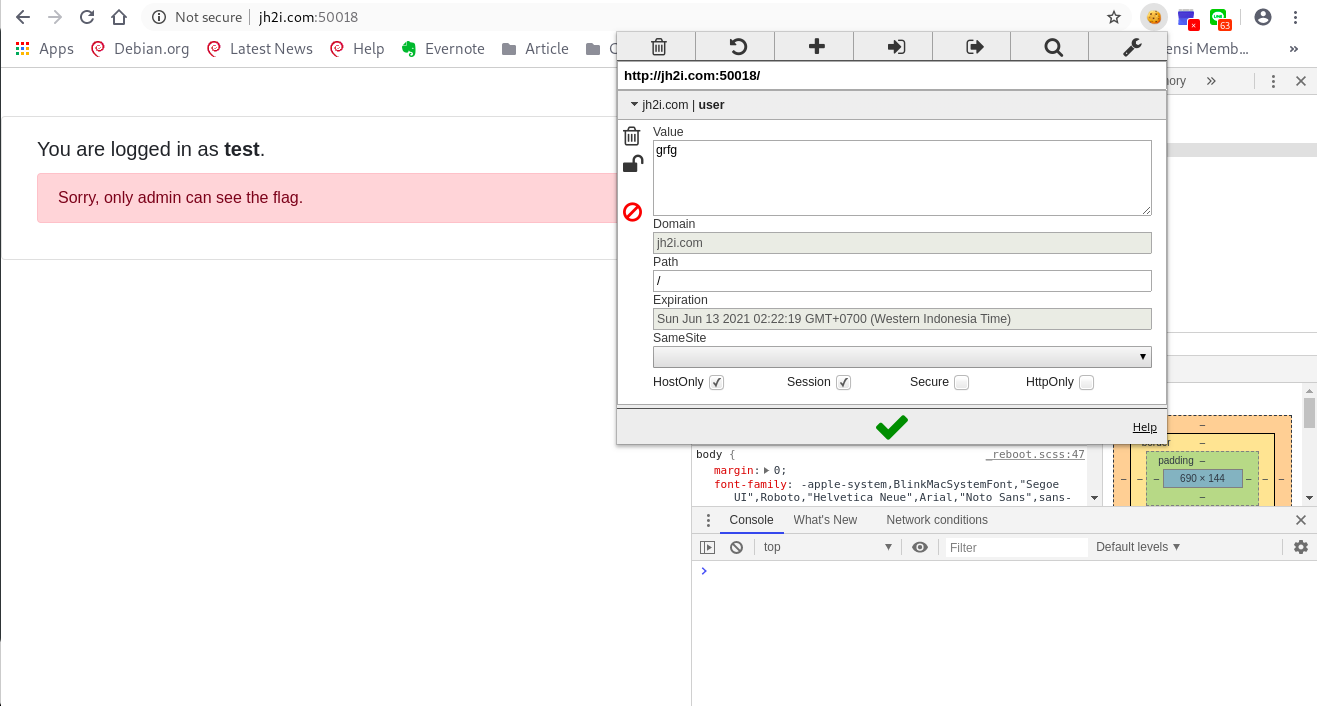
From the picture, we can see that the cookie is “grfg”, where we will get the user as “test”. But if we try to change the cookie to “test”, we will get the user “grfg”.
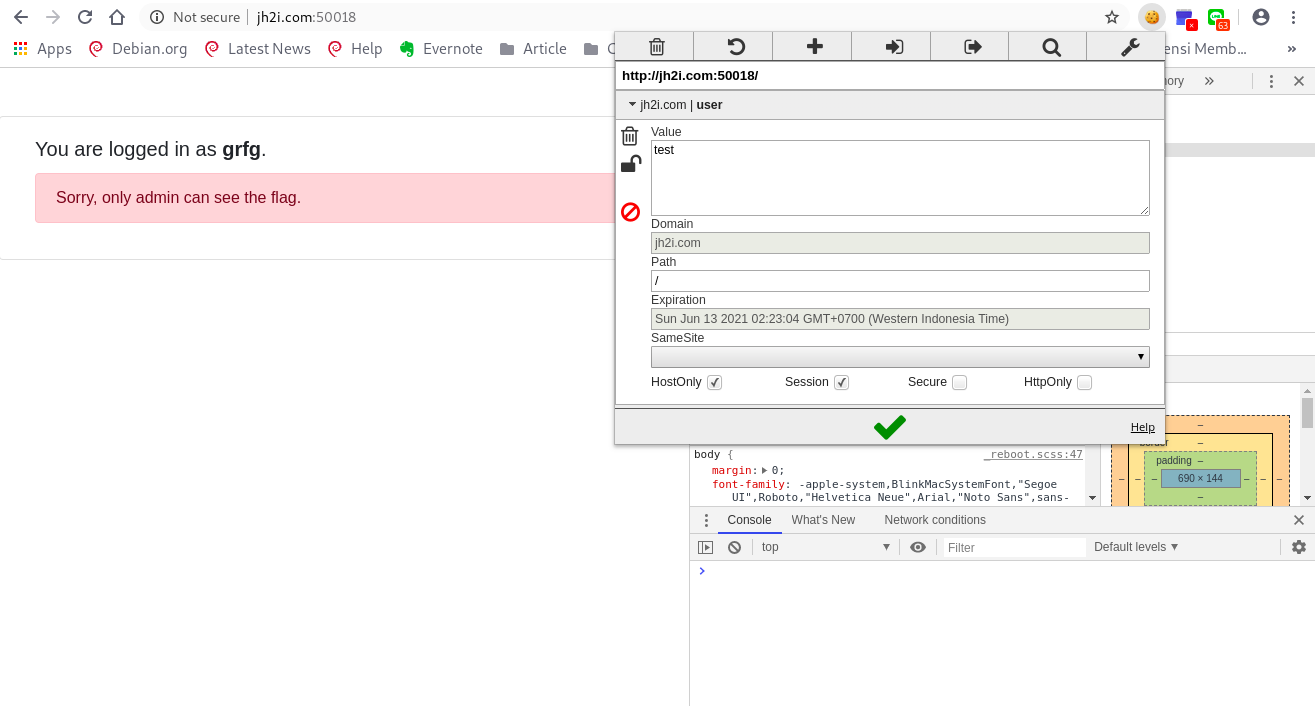
From the result, i found that: test -> encrypted -> grfg -> decrypted -> ‘test’
Assumed that the key is 13. We can encrypt “admin” using the code below:
1
python3 -c 'encrypt = [chr(((ord(char)-97+13)%26)+97) for char in admin];print(.join(encrypt))'
and if we insert it to our cookies after we login to user “test”, the results will show us our flag:

Flag
Flag : flag{H4cK_aLL_7H3_C0okI3s}
Easy Kessy
Description
Dang it, not again…
Download the file below.
Problem
The problem is th file type has this kind of type:
1
easy_keesy: Keepass password database 2.x KDBX
Based on my research on google, i found this website https://sourceforge.net/p/keepass/discussion/329220/thread/17d1bd26/. This website has explanatioin about the command that we can use to open the file.
1
2
3
sudo apt-add-repository ppa:jtaylor/keepass
sudo apt-get update
sudo apt-get install keepass2
After installing the tools, i try to open the file using keepass2. But it will need master key to get access to the file.
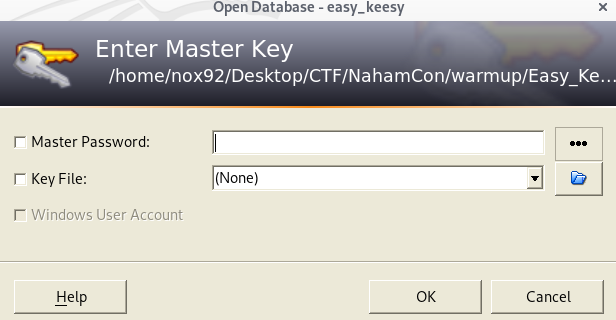
Then i search on google an found this article https://madcityhacker.com/2018/11/04/cracking-keepass-databases-with-hashcat/, where it show us that the file keepass can be crack using hashcat.
1
hashcat -a 0 -m 13400 encrypted.txt /usr/share/wordlists/rockyou.txt --force
1
$keepass$*2*100000*0*d92288b1c51244a6b5adf65895aef924ddc083a819e0dbd387e7b842649c7974*af85267b1972de6c67cd4fa43d6b4d1b212516d4acd801643e8440f043332477*2d587ad4c839c1d2265525946215fb7e*215547d465bc6fb180a17abbd51625c4c3159b555d880d95400002355f7e2ab8*fbdc2c7d91a59d942e71d6b4d089e3ecbea5a2ab4d86094a6e777626b8779504:monkeys
Based on our results on the netcat, the password is monkeys. Using the password, will give us access to the file.

After a bit googling, i found this article https://sourceforge.net/p/keepass/discussion/329221/thread/2e98502c/, where it tell us that the keepass has an ooption to change the password from asterisks symbol to plain text. We only need to uncheck hide asterisks in configure columns -> password -> uncheck hide asterisks.
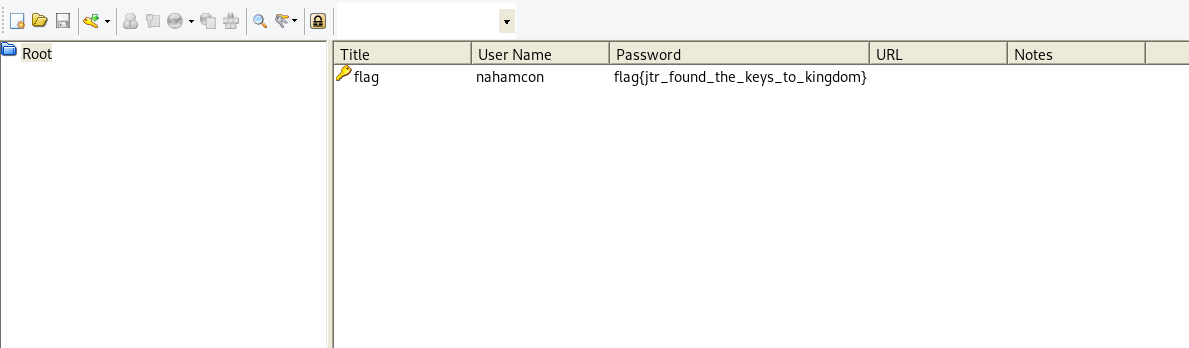
Flag
Flag : flag{jtr_found_the_keys_to_kingdom}
Metameme
Description
Hacker memes. So meta.
Download the file below.
Solution
To solve this challenge, first i open the image that i downloaded:

Then i run the exiftool command to see the meta data as the challenge name:
1
exiftool hackermeme.jpg | grep -oE "flag{.*}"
Flag
Flag : flag{N0t_7h3_4cTuaL_Cr3At0r}
CLIsay
Description
cowsay is hiding something from us!
Download the file below.
Problem
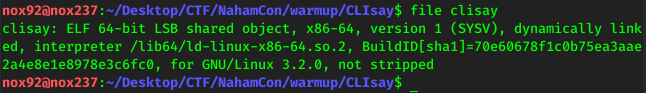
To solve this challenge, first i download the file.
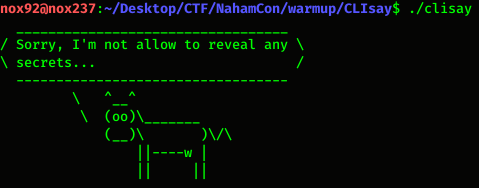
Solution
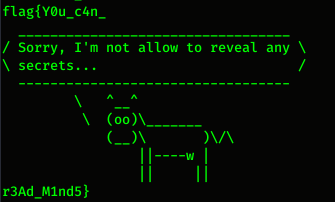
Then to solve this challenge, i using this command :
1
echo "$(strings clisay | grep -oE flag{.*)$(strings clisay | grep -oE .*})"
Flag
flag : flag{Y0u_c4n_r3Ad_M1nd5}
Read The Rules
Description
Please follow the rules for this CTF!
Connect here: https://ctf.nahamcon.com/rules
Solution
To found this flag, we only need to inspect element using developer tools from the browser:

Flag
Flag : flag{we_hope_you_enjoy_the_game}