On March 13th, I was playing Nahamcon CTF where I learn Capture the Flag again for a while and here’s my writeup for the challenges that I managed to solve (except for the “Read the Rules” challenge).
resourceful
Description
I built my first ever android app with authentication!
Problem
From the android phone, I installed the .apk file and find that we need to insert the password.
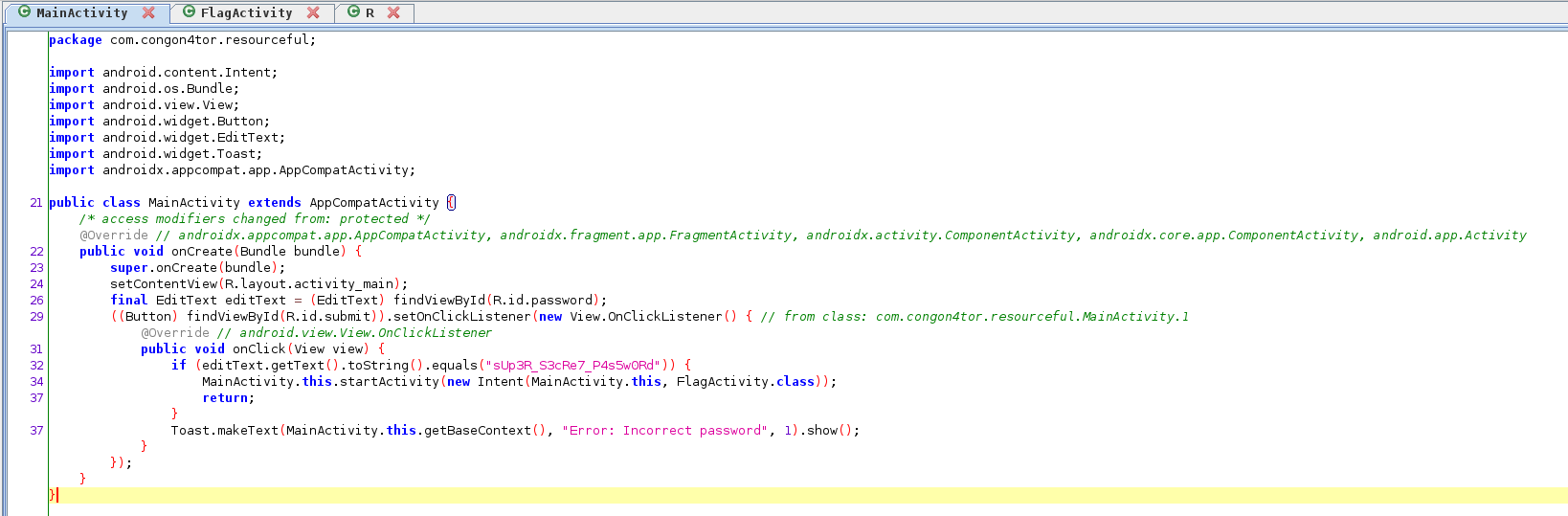
To solve this challenge, I used jadx-gui to open the apk file into java programming language where I manage to find the password inside the .apk file, which is “sUp3R_S3cRe7_P4s5w0Rd”
Inserting the password into our input will give us the password.
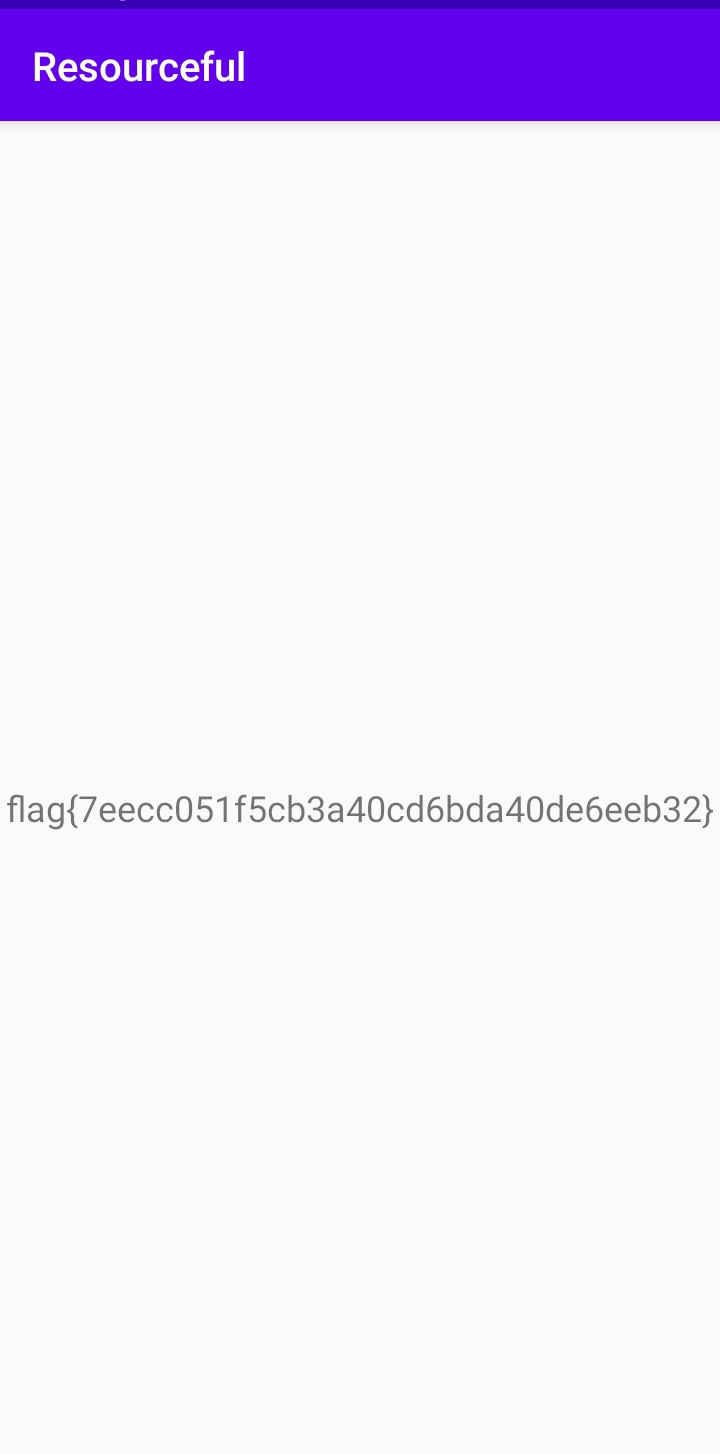
Flag
Flag : flag{7eecc051f5cb3a40cd6bda40de6eeb32}
andra
Description
You know what to do. :)
Problem
For this challenge, I used apktool to decode the .apk file and I find that the flag by using grep command.
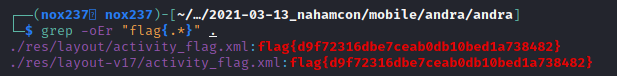
Flag
Flag : flag{d9f72316dbe7ceab0db10bed1a738482}
bionic
Description
Thank you for taking on The Mission. You can begin by exploring the CONSTELLATIONS public website, constellations.page.
CONSTELLATIONS has “tried” to reduce their attack surface by offering just a static website. But you might find some low-hanging fruit to get you started.
You should find the flag for this challenge ON THIS constellations.page website.
With the flag of this challenge, you should also find a new URL that will assist in the next challenge.
After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.
Problem
For the challenge, I visit the url that has been given: https://constellations.page/, where I find this website
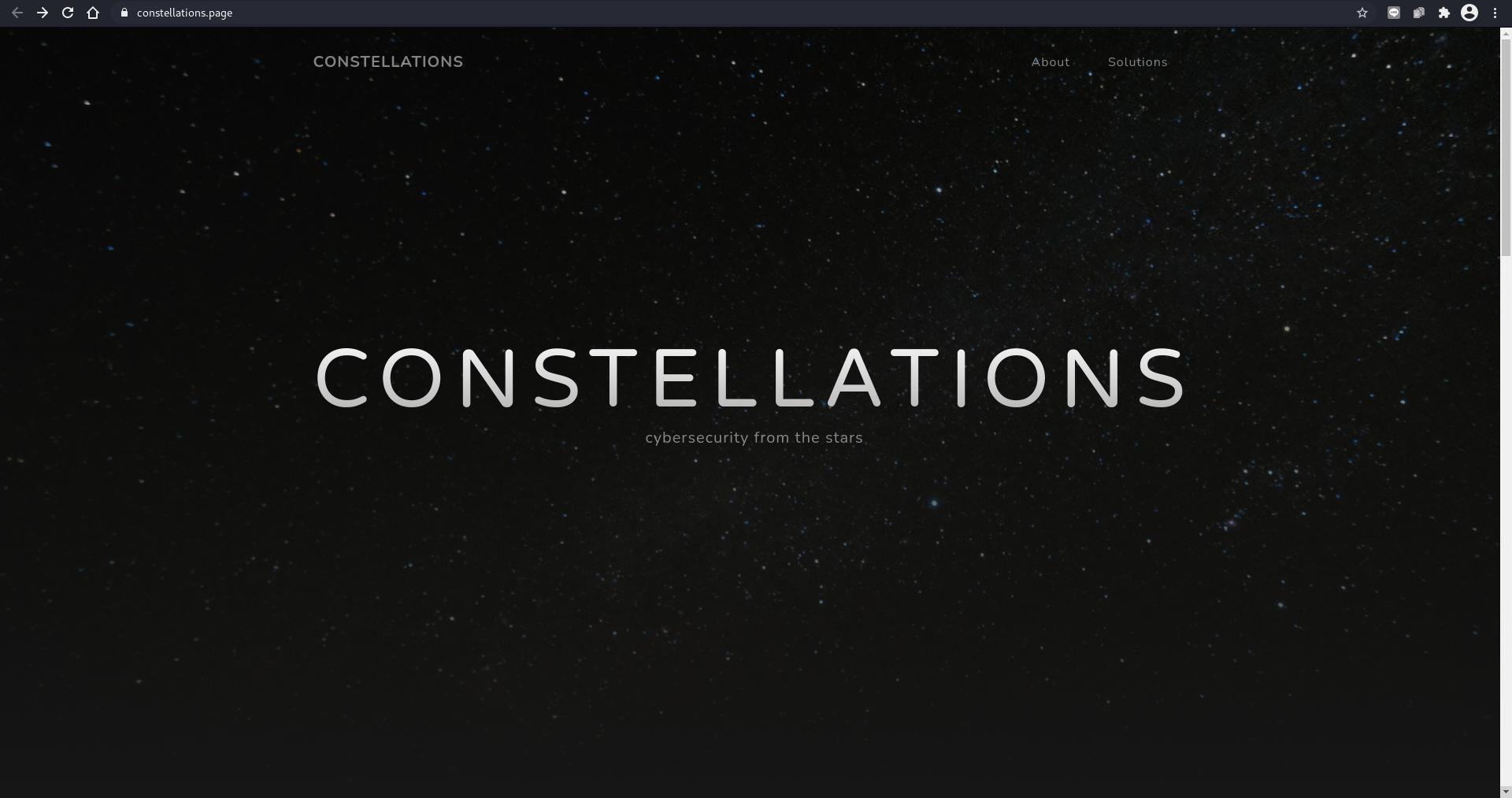
I search for the flag but I didn’t find one in the website. So I visit the robots.txt file where the flag was located in there.
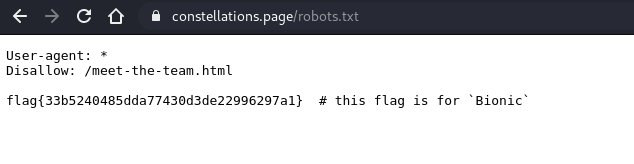
In robots.txt, it also have another html page that link to another challenge.
Flag
Flag : flag{33b5240485dda77430d3de22996297a1}
The Mission
Description
Enter the flag you find on The Mission page to open the gates and unlock challenges for The Mission. Please note, your participation in “The Mission” serves as permission for us to share your e-mail address with our sponsors, for potential career opportunities and private invitations to vulnerability disclosure and bug bounty programs.
After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.
Problem
By inspect element on the website, I managed to find the flag.
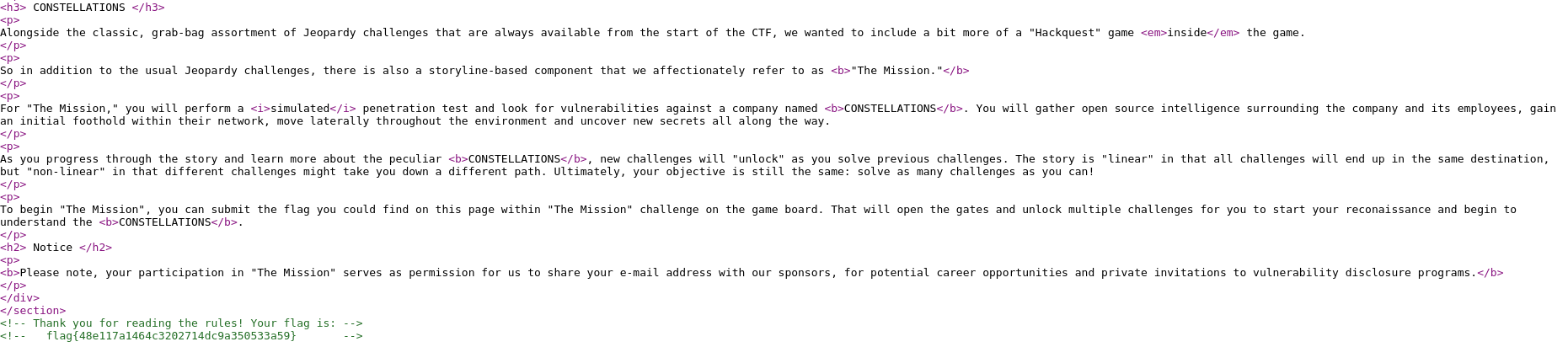
Flag
Flag : flag{48e117a1464c3202714dc9a350533a59}
Chicken Wings
Description
I ordered chicken wings at the local restaurant, but uh… this really isn’t what I was expecting…
Problem
From the text, I only find this:
1
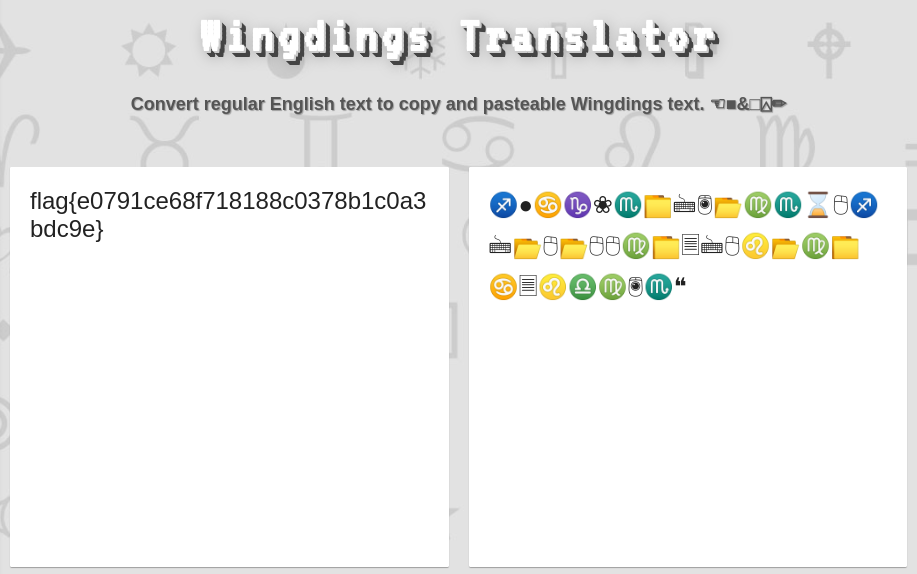
♐●♋♑❀♏📁🖮🖲📂♍♏⌛🖰♐🖮📂🖰📂🖰🖰♍📁🗏🖮🖰♌📂♍📁♋🗏♌♎♍🖲♏❝
Where it might be related to the font that we are using. Then I try to search for wingding translator and I found this: https://lingojam.com/WingdingsTranslator. Inserting the text will give us the flag.
Flag
Flag: flag{e0791ce68f718188c0378b1c0a3bdc9e}
buzz
Description
You know, that sound that bumblebees make?
Problem
When I running file command, I found the output was compress’d data 16 bits. Then I try to search on internet, where I find this stackoverflow question: https://stackoverflow.com/questions/12168081/how-can-i-uncompress-z-file-under-ubuntu.
Turns out that compress’d data 16 bits was .z extension which is a UNIX Compressed file. Like other archive file formats, Z files are used to compress a file for backup/archive purposes. However, unlike more complex formats, Z files can store just one file and no folders. https://www.lifewire.com/z-file-2622674 To decompress the file, we can run uncompress buzz and I found the flag.
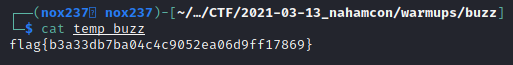
Flag
Flag : flag{b3a33db7ba04c4c9052ea06d9ff17869}
esab64
Description
Was it a car or a cat I saw?
Problem
Base on the text file that I found, I see that the task is we need to decode the text using base64. So I try to decode it in the terminal and found this:
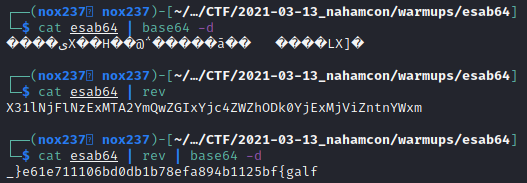
From there I manage to find the flag by reversing it. The final command is : cat esab64 | rev | base64 -d | rev
Flag
Flag : flag{fb5211b498afe87b1bd0db601117e16e}
pollex
Description
👍
Problem
To solve this challenge, I try to run exiftool and steghide, but I didn’t find anything useful in there. So I run binwalk where I find interesting files in there.
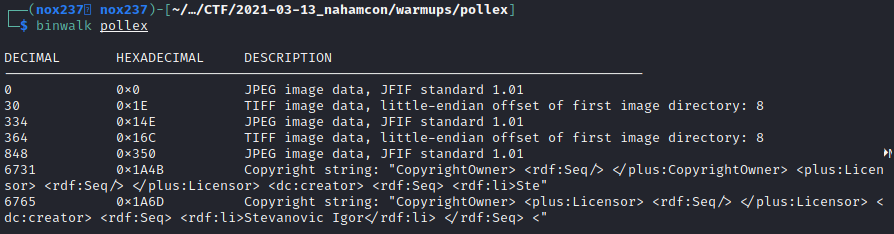
After a bit searching on the internet, I found that we can extract the files by running binwalk --dd=".*" pollex (https://stackoverflow.com/questions/36530643/use-binwalk-to-extract-all-files). After extracting all the files, I found one of the files contain the flag that we are searching for.

Flag
Flag : flag{65c34a1ec121a286600ddd48fe36bc00}
shoelaces
Description
Do you double-knot your shoelaces? You gotta keep’em tied!
Problem
Based on the shoelaces.jpg file, I didn’t found anything usefull from exif command. I also didn’t find file that inside the file that I try to extract it using steghide. Then I try to run strings command and turns out that the flag was there.
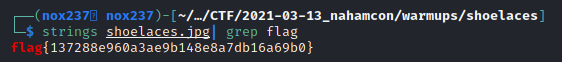
Flag
Flag: flag{137288e960a3ae9b148e8a7db16a69b0}
Homeward Bound
Description
I can’t get anything out of this website… can you find anything interesting?
NOTE: That message in intended. This challenge is working as it should.
Problem
By visiting the website, I found this website:
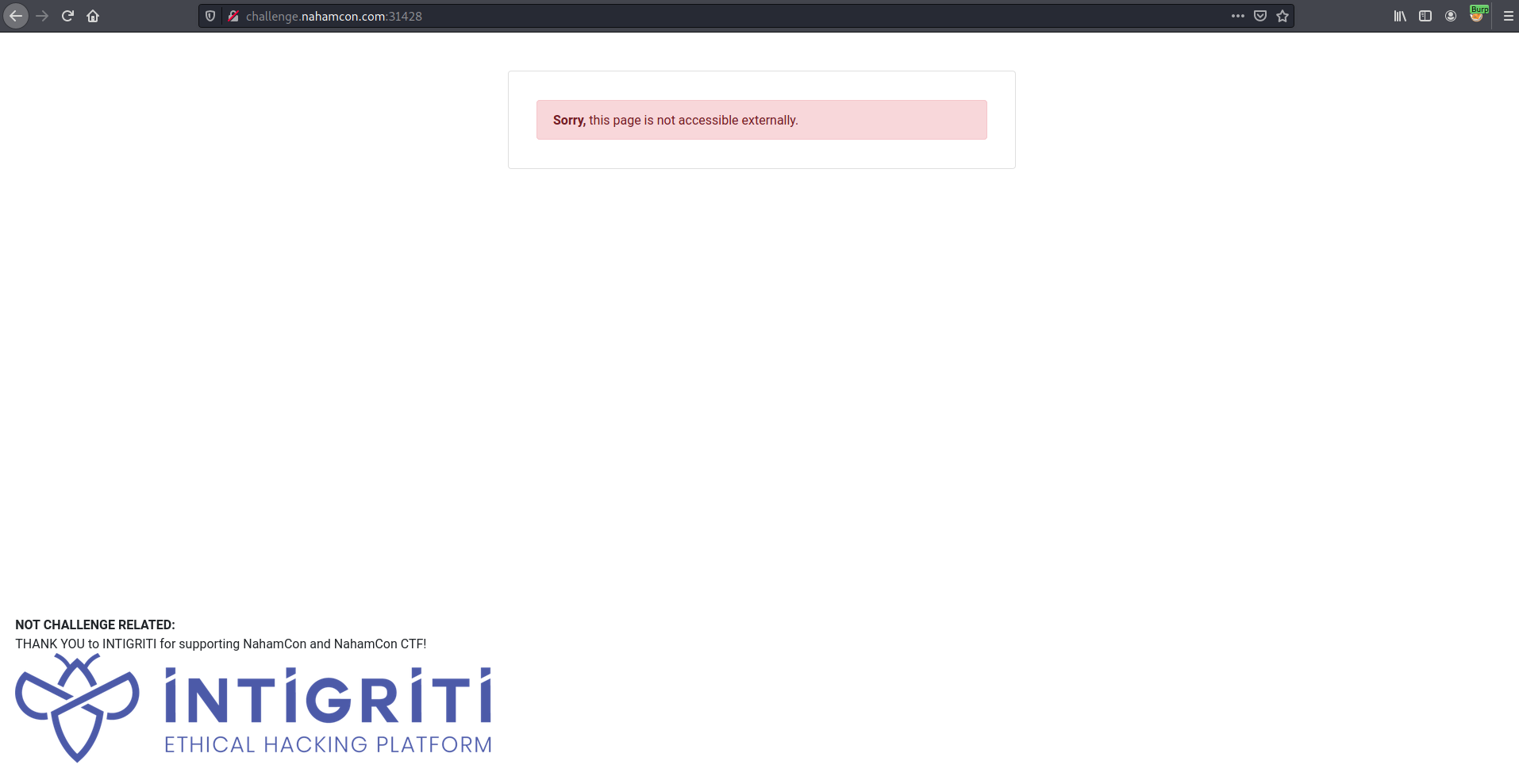
By looking at other CTF writeups (https://medium.com/@Mr_R0w07/glug-ctf-web-writeup-490c8448d484), I found that there is X-Forwarded-For http header that can be used to identifying the originating IP address of a client connecting to a web server through an HTTP proxy or load balancer.
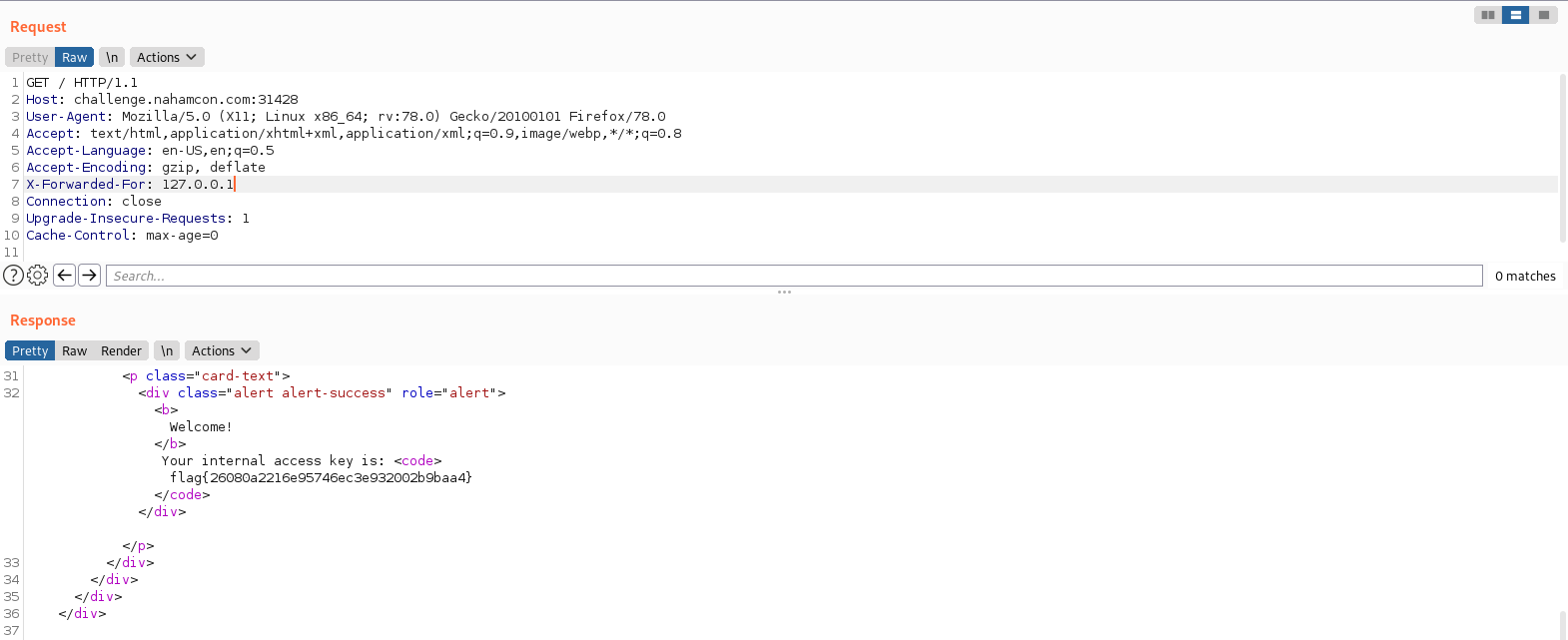
By inserting this to burpsuite, I managed to found the flag.
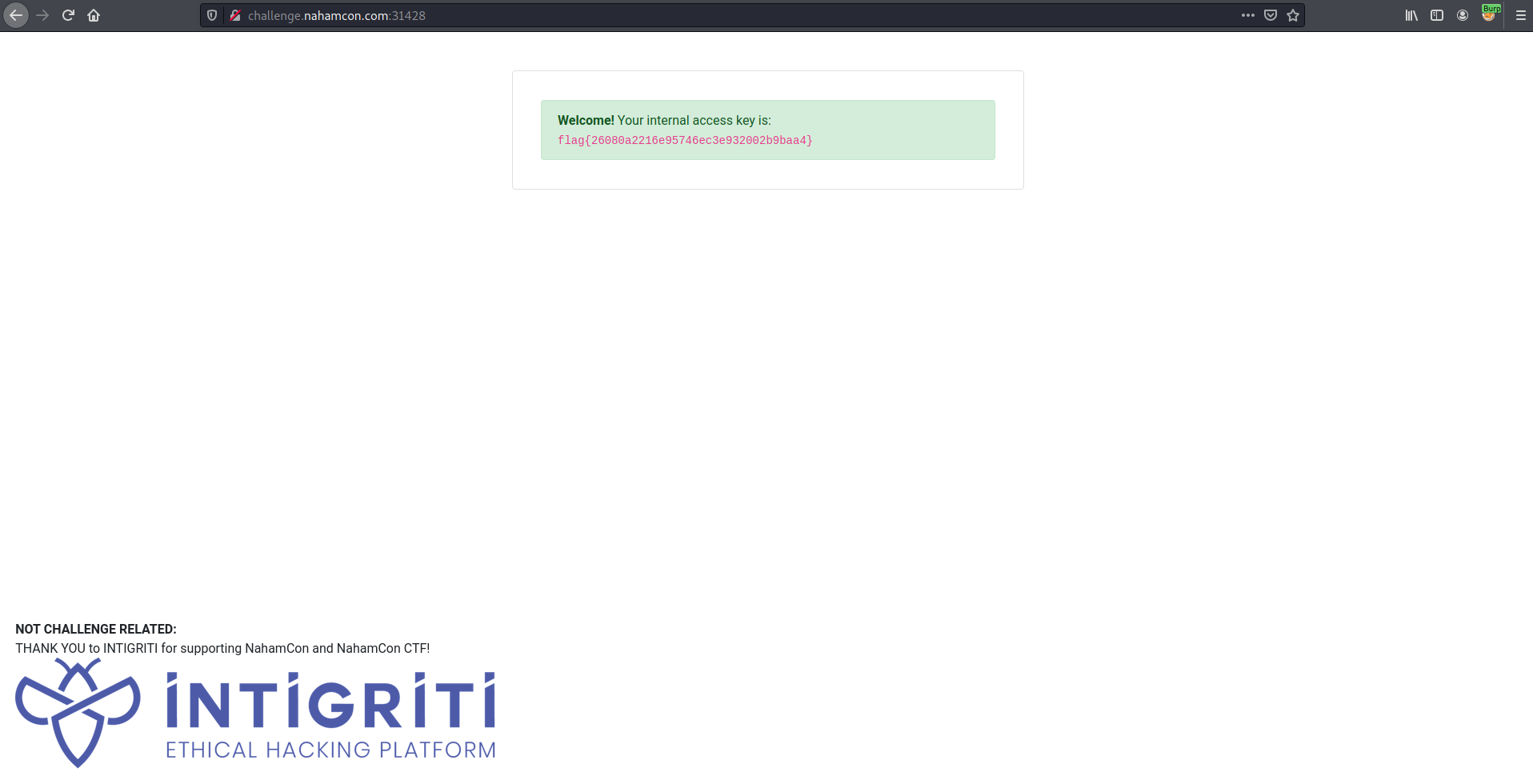
Flag
Flag : flag{26080a2216e95746ec3e932002b9baa4}