Bandit Level 0
Description
The goal of this level is for you to log into the game using SSH. The host to which you need to connect is bandit.labs.overthewire.org, on port 2220. The username is bandit0 and the password is bandit0. Once logged in, go to the Level 1 page to find out how to beat Level 1.
Commands
SSH
Solution
By connecting through SSH and cat the readme file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit0", port=2220, password="bandit0", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
sh.sendline(b"cat readme")
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()
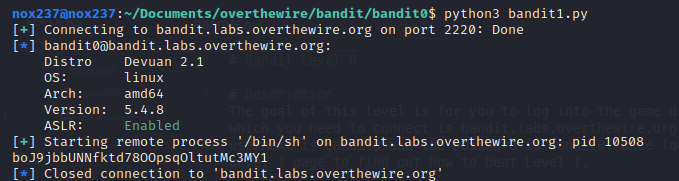
When execute, it will look like this.
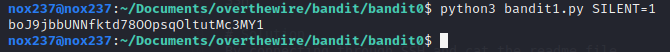
If we want to disable without logging, we can execute like this.
References
- https: // github.com / Gallopsled / pwntools / issues / 627
- https: // docs.pwntools.com / en / stable / tubes / ssh.html
Bandit Level 1
Description
The password for the next level is stored in a file called - located in the home directory
Commands
ls, cd, cat, file, du, find
Solution
Looking the shell, we can get:
1
2
3
4
5
6
7
8
bandit1@bandit:~$ ls -la
total 24
-rw-r----- 1 bandit2 bandit1 33 May 7 20:14 -
drwxr-xr-x 2 root root 4096 May 7 20:14 .
drwxr-xr-x 41 root root 4096 May 7 20:14 ..
-rw-r--r-- 1 root root 220 May 15 2017 .bash_logout
-rw-r--r-- 1 root root 3526 May 15 2017 .bashrc
-rw-r--r-- 1 root root 675 May 15 2017 .profile
If we “cat” the /etc/bandit_pass/bandit1, we can get the flag. So our get flag script will be like this.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit1", port=2220, password="boJ9jbbUNNfktd78OOpsqOltutMc3MY1", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
# sh.interactive()
sh.sendline(b"cat /etc/bandit_pass/bandit1")
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()
Bandit Level 2
Description
The password for the next level is stored in a file called spaces in this filename located in the home directory
Commands
ls, cd, cat, file, du, find
Solution
If we see the /home/bandit2, we will get:
1
2
3
4
5
6
7
total 24
drwxr-xr-x 2 root root 4096 May 7 20:14 .
drwxr-xr-x 41 root root 4096 May 7 20:14 ..
-rw-r--r-- 1 root root 220 May 15 2017 .bash_logout
-rw-r--r-- 1 root root 3526 May 15 2017 .bashrc
-rw-r--r-- 1 root root 675 May 15 2017 .profile
-rw-r----- 1 bandit3 bandit2 33 May 7 20:14 spaces in this filename
Then we can cat the file by using “cat ./’spaces in this filename’”. The “get flag script” will be like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit2", port=2220, password="CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
sh.sendline(b'cat ./"spaces in this filename"')
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()
Bandit Level 3
Description
The password for the next level is stored in a hidden file in the inhere directory.
Commands you may need to solve this level
ls, cd, cat, file, du, find
Solution
By looking at the description, we will see the hidden file in the directory of “inhere”.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ ls - la
total 24
drwxr - xr - x 3 root root 4096 May 7 20: 14 .
drwxr - xr - x 41 root root 4096 May 7 20: 14 ..
-rw - r - -r - - 1 root root 220 May 15 2017 .bash_logout
-rw - r - -r - - 1 root root 3526 May 15 2017 .bashrc
-rw - r - -r - - 1 root root 675 May 15 2017 .profile
drwxr - xr - x 2 root root 4096 May 7 20: 14 inhere
$ ls inhere
$ ls - la inhere
total 12
drwxr - xr - x 2 root root 4096 May 7 20: 14 .
drwxr - xr - x 3 root root 4096 May 7 20: 14 ..
-rw - r - ---- 1 bandit4 bandit3 33 May 7 20: 14 .hidden
Then, we can cat the file with the command “cat ./inhere/.hidden”. The “get flag script” will be like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit3", port=2220, password="UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
sh.sendline(b'cat ./inhere/.hidden')
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()
Bandit Level 4
Description
The password for the next level is stored in the only human-readable file in the inhere directory. Tip: if your terminal is messed up, try the “reset” command.
Commands
ls, cd, cat, file, du, find
Solution
By looking the files in folder “inhere”. We can see that the there is a hex value inside the file, so when we the file, it will look like this:
1
2
3
4
5
6
$ ls inhere
-file00 -file02 -file04 -file06 -file08
-file01 -file03 -file05 -file07 -file09
$ cat inhere/*
\xea/`\x07ғ\x1b}\xa6%\xbb\x9crL\x035\xf6g\x82\xc1\x86 \x8c\x95\x8f\xd5\xd\xa3\xbf\xccp,k\xca;\xb4\xb0r*\xc0\xdf \x1c.!\xe7\xddC\xe1\xc9J\x03\xa8dx,\xc8e\xd9)\xe3#\xf1\xf75\xac\x15\x05\x04\xaap\xa7\xc9V\xd4_\x90\xc8\xdfׯ\xc3mm\xf0\xcc\xf8\xba\xe4\xf7h\x0fTQO\xcc`\x864\x19"aל\xa9߂phT\x94\xfe,\xe8Ai\xf74\xef\xafו$\xf4\x9d\x93\xc5I&\x8e\x80\xa4\xbf\xea\xf0\xafc\x90\x9c\xf9ގ.\xd1\x06?\x93\x8ar\xb6l\x03$\xd2?h\xe19('\xab\xa8\x93!y\xbfe\xb2#\x8ex\xd8O\x87\xd6=\xe0\x89ly\xb5\xc3\xc7~\xa5\xa1A\xa3f\xc3\xbb\xc6\xce-E\xa7{\xa6\xd3\xc9m\x98\x8a\xc4\xc4\xf4ܗMkoReBOKuIDDepwhWk7jZC0RTdopnAYKh
\xdbT\x80?\xebi\xa7\xd4j\xed\x9e\xcaîP\xa3F\xe5l\xf9n\x8a\x1cJ\xda\xeb\xcd\xd0{\xce\xd0@\x1de\xf00$\xa6in=\xc7\xed_\x1d\xdf5F\x16\xa4P7\xfsz\xba\x91gN
But if we print the character using command like grep or strings, we can get the human-readable file.
1
2
3
4
5
6
7
8
9
10
11
$ grep . inhere/*
inhere/-file00:\xea/`\x07ғ\x1b}\xa6%\xbb\x9crL\x035\xf6g\x82\xc1\x86 \x8c\x95\x8f\xd5\xd\xa3
inhere/-file01:\xbf\xccp,k\xca;\xb4\xb0r*\xc0\xdf \x1c.!\xe7\xddC\xe1\xc9J\x03\xa8dx,\xc8
inhere/-file02:e\xd9)\xe3#\xf1\xf75\xac\x15\x05\x04\xaap\xa7\xc9V\xd4_\x90\xc8\xdfׯ\xc3mm
inhere/-file03:\xf0\xcc\xf8\xba\xe4\xf7h\x0fTQO\xcc`\x864\x19"aל\xa9߂phT\x94\xfe,\xe8A
inhere/-file04:i\xf74\xef\xafו$\xf4\x9d\x93\xc5I&\x8e\x80\xa4\xbf\xea\xf0\xafc\x90\x9c\xf9ގ.\xd1\x06?\x93
inhere/-file05:\x8ar\xb6l\x03$\xd2?h\xe19('\xab\xa8\x93!y\xbfe\xb2#\x8ex\xd8O\x87\xd6=\xe0\x89
inhere/-file06:ly\xb5\xc3\xc7~\xa5\xa1A\xa3f\xc3\xbb\xc6\xce-E\xa7{\xa6\xd3\xc9m\x98\x8a\xc4\xc4\xf4ܗM
inhere/-file07:koReBOKuIDDepwhWk7jZC0RTdopnAYKh
inhere/-file08:\xdbT\x80?\xebi\xa7\xd4j\xed\x9e\xcaîP\xa3F\xe5l\xf9n\x8a\x1cJ\xda\xeb\xcd\xd0{\xce\xd0@
inhere/-file09:\x1de\xf00$\xa6in=\xc7\xed_\x1d\xdf5F\x16\xa4P7\xfsz\xba\x91gN
So our “get flag script” will be like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit4", port=2220, password="pIwrPrtPN36QITSp3EQaw936yaFoFgAB", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
sh.sendline(b'strings ./inhere/* | tail -n 1')
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()
Bandit Level 5
Description
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties:
- human-readable
- 1033 bytes in size
- not executable
Commands
ls, cd, cat, file, du, find
Solution
If we see the inhere folder, we will get many files and directories.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
total 24
drwxr-xr-x 3 root root 4096 May 7 20:15 .
drwxr-xr-x 41 root root 4096 May 7 20:14 ..
-rw-r--r-- 1 root root 220 May 15 2017 .bash_logout
-rw-r--r-- 1 root root 3526 May 15 2017 .bashrc
-rw-r--r-- 1 root root 675 May 15 2017 .profile
drwxr-x--- 22 root bandit5 4096 May 7 20:15 inhere
./inhere:
total 88
drwxr-x--- 22 root bandit5 4096 May 7 20:15 .
drwxr-xr-x 3 root root 4096 May 7 20:15 ..
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere00
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere01
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere02
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere03
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere04
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere05
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere06
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere07
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere08
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere09
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere10
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere11
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere12
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere13
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere14
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere15
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere16
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere17
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere18
drwxr-x--- 2 root bandit5 4096 May 7 20:15 maybehere19
./inhere/maybehere00:
total 72
-rwxr-x--- 1 root bandit5 1039 May 7 20:15 -file1
-rw-r----- 1 root bandit5 9388 May 7 20:15 -file2
-rwxr-x--- 1 root bandit5 7378 May 7 20:15 -file3
drwxr-x--- 2 root bandit5 4096 May 7 20:15 .
drwxr-x--- 22 root bandit5 4096 May 7 20:15 ..
-rwxr-x--- 1 root bandit5 551 May 7 20:15 .file1
-rw-r----- 1 root bandit5 7836 May 7 20:15 .file2
-rwxr-x--- 1 root bandit5 4802 May 7 20:15 .file3
-rwxr-x--- 1 root bandit5 6118 May 7 20:15 spaces file1
-rw-r----- 1 root bandit5 6850 May 7 20:15 spaces file2
-rwxr-x--- 1 root bandit5 1915 May 7 20:15 spaces file3
./inhere/maybehere01:
total 80
-rwxr-x--- 1 root bandit5 6028 May 7 20:15 -file1
-rw-r----- 1 root bandit5 288 May 7 20:15 -file2
-rwxr-x--- 1 root bandit5 9641 May 7 20:15 -file3
drwxr-x--- 2 root bandit5 4096 May 7 20:15 .
drwxr-x--- 22 root bandit5 4096 May 7 20:15 ..
-rwxr-x--- 1 root bandit5 8944 May 7 20:15 .file1
-rw-r----- 1 root bandit5 3070 May 7 20:15 .file2
-rwxr-x--- 1 root bandit5 3792 May 7 20:15 .file3
-rwxr-x--- 1 root bandit5 4139 May 7 20:15 spaces file1
-rw-r----- 1 root bandit5 4543 May 7 20:15 spaces file2
-rwxr-x--- 1 root bandit5 8834 May 7 20:15 spaces file3
...
./inhere/maybehere18:
total 68
-rwxr-x--- 1 root bandit5 9697 May 7 20:15 -file1
-rw-r----- 1 root bandit5 77 May 7 20:15 -file2
-rwxr-x--- 1 root bandit5 2306 May 7 20:15 -file3
drwxr-x--- 2 root bandit5 4096 May 7 20:15 .
drwxr-x--- 22 root bandit5 4096 May 7 20:15 ..
-rwxr-x--- 1 root bandit5 5702 May 7 20:15 .file1
-rw-r----- 1 root bandit5 2084 May 7 20:15 .file2
-rwxr-x--- 1 root bandit5 154 May 7 20:15 .file3
-rwxr-x--- 1 root bandit5 7334 May 7 20:15 spaces file1
-rw-r----- 1 root bandit5 6348 May 7 20:15 spaces file2
-rwxr-x--- 1 root bandit5 7040 May 7 20:15 spaces file3
./inhere/maybehere19:
total 76
-rwxr-x--- 1 root bandit5 6302 May 7 20:15 -file1
-rw-r----- 1 root bandit5 5594 May 7 20:15 -file2
-rwxr-x--- 1 root bandit5 7965 May 7 20:15 -file3
drwxr-x--- 2 root bandit5 4096 May 7 20:15 .
drwxr-x--- 22 root bandit5 4096 May 7 20:15 ..
-rwxr-x--- 1 root bandit5 7209 May 7 20:15 .file1
-rw-r----- 1 root bandit5 4740 May 7 20:15 .file2
-rwxr-x--- 1 root bandit5 494 May 7 20:15 .file3
-rwxr-x--- 1 root bandit5 7186 May 7 20:15 spaces file1
-rw-r----- 1 root bandit5 8785 May 7 20:15 spaces file2
-rwxr-x--- 1 root bandit5 2307 May 7 20:15 spaces file3
By inserting the file with the command “cat $(find inhere -size 1033c ! -executable) | head -n 1”
1
2
$ cat $(find inhere -size 1033c ! -executable) | head -n 1
DXjZPULLxYr17uwoI01bNLQbtFemEgo7
So our “get flag script” will be like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit5", port=2220, password="koReBOKuIDDepwhWk7jZC0RTdopnAYKh", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
sh.sendline(b'cat $(find inhere -size 1033c ! -executable) | head -n 1')
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()
References
- https://unix.stackexchange.com/questions/43148/unix-commands-find
- https://www.simplified.guide/linux/list-files-recursively#:~:text=Steps%20to%20list%20files%20in,Use%20ls%20with%20%2DR%20option.&text=Use%20find%20with%20%2Dls%20or%20%2Dprint%20option.
Bandit Level 6
Description
The password for the next level is stored somewhere on the server and has all of the following properties:
- owned by user bandit7
- owned by group bandit6
- 33 bytes in size
Commands
ls, cd, cat, file, du, find, grep
Solution
Looking at the task, we can use the find command to search with the given criteria.
1
2
$ find / -user bandit7 -group bandit6 -size 33c 2>/dev/null
/var/lib/dpkg/info/bandit7.password
So our “get flag script” is:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit6", port=2220, password="DXjZPULLxYr17uwoI01bNLQbtFemEgo7", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
sh.sendline(b'cat $(find / -user bandit7 -group bandit6 -size 33c 2>/dev/null)')
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()
Bandit Level 7
Description
The password for the next level is stored in the file data.txt next to the word millionth
Commands
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Solution
To get the flag, we can use grep to find the millionth
1
2
3
4
$ cat data.txt | wc -l
98567
$ cat data.txt | grep millionth
millionth cvX2JJa4CFALtqS87jk27qwqGhBM9plV
Our get flag script will look like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit7", port=2220, password="HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
sh.sendline(b"echo $(cat data.txt | grep millionth) | cut -d ' ' -f 2")
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()
Bandit Level 8
Description
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
Commands
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Solution
Using the sort and uniq, we can get the unique line from the result:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ sort data.txt | uniq -c
...
10 TKUtQbeYnEzzYIne7BinoBx2bHFLBXzG
10 TThRArdF2ZEXMO47TIYkyPPLtvzzLcDf
10 U0NYdD3wHZKpfEg9qGQOLJimAJy6qxhS
10 UASW6CQwD6MRzftu6FAfyXBK0cVvnBLP
10 UJiCNvDNfgb3fcCj8PjjnAXHqUM63Uyj
10 UVnZvhiVQECraz5jl8U14sMVZQhjuXia
10 UjsVbcqKeJqdCZQCDMkzv6A9X7hLbNE4
1 UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR
10 V2d9umHiuPLYLIDsuHj0frOEmreCZMaA
10 VkBAEWyIibVkeURZV5mowiGg6i3m7Be0
10 WBqr9xvf6mYTT5kLcTGCG6jb3ex94xWr
10 X1JHOUkrb4KgugMXIzMWWIWvRkeZleTI
10 XyeJdbrUJyGtdGx8cXLQST0pwu5cvpcA
10 Z9OC6DQpppreChPhwRJJV9YYTtrxNVcO
10 aR2QhaBoDMncvJqPWkvLXMzEx9meBIbX
10 bRnktwNdxFy2RPZIshXJikswwEzJGvJ9
10 cIPbot7oYveUPNxDMhv1hiri50CqpkTG
...
We can also print the result by using the command:
1
2
$ sort data.txt | uniq -u
UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR
If we not using sort, we will get the count for every line is one.
1
2
3
4
5
6
7
8
9
10
$ cat data.txt | uniq -c
1 VkBAEWyIibVkeURZV5mowiGg6i3m7Be0
1 zdd2ctVveROGeiS2WE3TeLZMeL5jL7iM
1 sYSokIATVvFUKU4sAHTtMarfjlZWWj5i
1 ySvsTwlMgnUF0n86Fgmn2TNjkSOlrV72
1 NLWvtQvL7EaqBNx2x4eznRlQONULlCYZ
1 LfrBHfAh0pP9bgGAZP4QrVkut3pysAYC
1 U0NYdD3wHZKpfEg9qGQOLJimAJy6qxhS
1 flyKxCbHB8uLTaIB5LXqQNuJj3yj00eh
...
Our “Get Flag Script” will be look like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit8", port=2220, password="cvX2JJa4CFALtqS87jk27qwqGhBM9plV", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
sh.sendline(b"sort data.txt | uniq -u")
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()
References
- https://www.computerhope.com/unix/uuniq.htm
- https://www.linuxjournal.com/content/back-basics-sort-and-uniq
Bandit Level 9
Description
The password for the next level is stored in the file data.txt in one of the few human-readable strings, preceded by several ‘=’ characters.
Commands
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Solution
If we using cat, we will get the hex value of the data.txt, so to get the human readable strings, we can use the strings command.
Then looking at the result and the ‘=’ character, we will get this:
1
2
3
4
5
6
7
8
9
10
11
12
$ strings data.txt | grep '='
========== the*2i"4
=:G e
========== password
<I=zsGi
Z)========== is
A=|t&E
Zdb=
c^ LAh=3G
*SF=s
&========== truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk
S=A.H&^
From our findings we can see the ‘=’ that have “2 or more” characters is the message.
1
2
3
4
5
$ strings data.txt | grep -E "[\w]*[=]{2,}[\w]*"
========== the*2i"4
========== password
Z)========== is
&========== truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk
From here, we can craft our get flag script in python3.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit9", port=2220, password="UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
sh.sendline(b'strings data.txt | grep -E "[\w]*[=]{2,}[\w]*" | tail -n 1 | cut -d " " -f 2')
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()
References
Bandit Level 10
Description
The password for the next level is stored in the file data.txt, which contains base64 encoded data
Commands
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Helpful
Solution
If we cat the data.txt, we will find this text:
1
2
$ cat data.txt
VGhlIHBhc3N3b3JkIGlzIElGdWt3S0dzRlc4TU9xM0lSRnFyeEUxaHhUTkViVVBSCg==
So to get the flag, we can use
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit10", port=2220, password="truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
sh.sendline("cat data.txt | base64 -d | cut -d ' ' -f 4".encode())
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()
Bandit Level 11
Description
The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
Commands
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Helpful
Solution
This data.txt was encrypted using rot13, so we can use tr to get the decrypt the rot13.
1
2
$ cat data.txt | tr "[A-Za-z]" "[N-ZA-Mn-za-m]"
The password is 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu
Then we can use python to make a script.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import pwn
# Connecting through SSH
r = pwn.ssh(user="bandit11", port=2220, password="IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR", host="bandit.labs.overthewire.org")
# Executing the /bin/sh on the server
sh = r.process('/bin/sh', env={"PS1": ""})
sh.sendline('cat data.txt | tr "[A-Za-z]" "[N-ZA-Mn-za-m]" | cut -d " " -f 4 '.encode())
# Getting the flag
flag = sh.recv()
print(flag.decode(), end="")
# Closed the SSH Connection
r.close()