talking_to_the_dead_2
Description
There’s a hidden flag that belongs to luciafer. Submit the contents of the hidden flag2.txt.
ssh hacktober@env.hacktober.io
Password: hacktober-Underdog-Truth-Glimpse
Solution
On the same directory as the challenge before (/home/luciafer/Documents), there is a hidden flag named .flag2.txt.
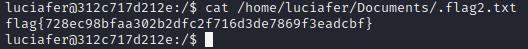
Flag
Flag : flag{728ec98bfaa302b2dfc2f716d3de7869f3eadcbf}
talking_to_the_dead_3
Description
Submit the contents of flag3.txt from the remote machine.
ssh hacktober@env.hacktober.io
Password: hacktober-Underdog-Truth-Glimpse
Solution
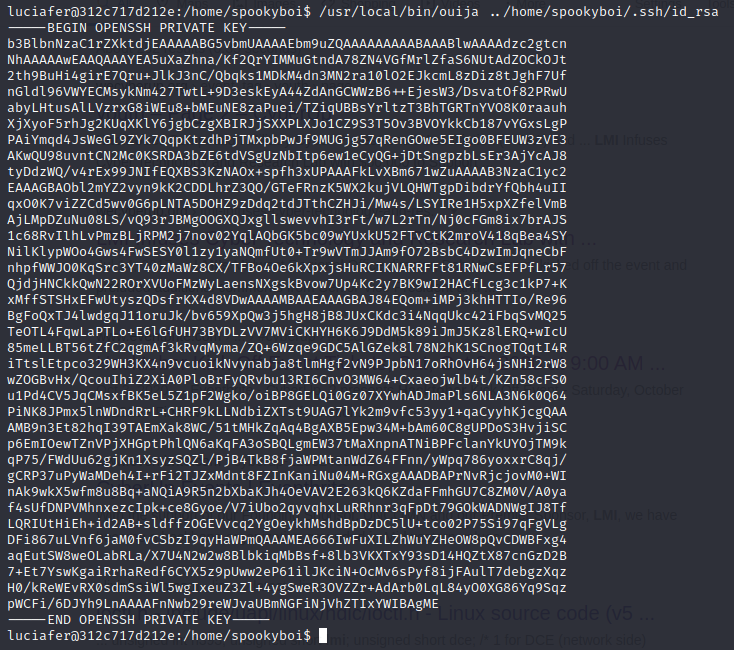
Before solving this challenge, i already solve the talking to the dead 4 where on that challenge i found out there is SUID binary where we can cat a file as root. Using this binary we can get our id_rsa to login as spookyboi
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEA5uXaZhna/Kf2QrYIMMuGtndA78ZN4VGfMrlZfaS6NUtAdZOCkOJt
2th9BuHi4girE7Qru+JlkJ3nC/Qbqks1MDkM4dn3MN2ra10lO2EJkcmL8zDiz8tJghF7Uf
nGldl96VWYECMsykNm427TwtL+9D3eskEyA44ZdAnGCWWzB6++EjesW3/DsvatOf82PRwU
abyLHtusAlLVzrxG8iWEu8+bMEuNE8zaPuei/TZiqUBBsYrltzT3BhTGRTnYVO8K0raauh
XjXyoF5rhJg2KUqXKlY6jgbCzgXBIRJjSXXPLXJo1CZ9S3T5Ov3BVOYkkCb187vYGxsLgP
PAiYmqd4JsWeGl9ZYk7QqpKtzdhPjTMxpbPwJf9MUGjg57qRenGOwe5EIgo0BFEUW3zVE3
AKwQU98uvntCN2Mc0KSRDA3bZE6tdVSgUzNbItp6ew1eCyQG+jDtSngpzbLsEr3AjYcAJ8
tyDdzWQ/v4rEx99JNIfEQXBS3KzNAOx+spfh3xUPAAAFkLvXBm671wZuAAAAB3NzaC1yc2
EAAAGBAObl2mYZ2vyn9kK2CDDLhrZ3QO/GTeFRnzK5WX2kujVLQHWTgpDibdrYfQbh4uII
qxO0K7viZZCd5wv0G6pLNTA5DOHZ9zDdq2tdJTthCZHJi/Mw4s/LSYIRe1H5xpXZfelVmB
AjLMpDZuNu08LS/vQ93rJBMgOOGXQJxgllswevvhI3rFt/w7L2rTn/Nj0cFGm8ix7brAJS
1c68RvIlhLvPmzBLjRPM2j7nov02YqlAQbGK5bc09wYUxkU52FTvCtK2mroV418qBea4SY
NilKlypWOo4Gws4FwSESY0l1zy1yaNQmfUt0+Tr9wVTmJJAm9fO72BsbC4DzwImJqneCbF
nhpfWWJO0KqSrc3YT40zMaWz8CX/TFBo4Oe6kXpxjsHuRCIKNARRFFt81RNwCsEFPfLr57
QjdjHNCkkQwN22ROrXVUoFMzWyLaensNXgskBvow7Up4Kc2y7BK9wI2HACfLcg3c1kP7+K
xMffSTSHxEFwUtyszQDsfrKX4d8VDwAAAAMBAAEAAAGBAJ84EQom+iMPj3khHTTIo/Re96
BgFoQxTJ4lwdgqJ11oruJk/bv659XpQw3j5hgH8jB8JUxCKdc3i4NqqUkc42iFbqSvMQ25
TeOTL4FqwLaPTLo+E6lGfUH73BYDLzVV7MViCKHYH6K6J9DdM5k89iJmJ5Kz8lERQ+wIcU
85meLLBT56tZfC2qgmAf3kRvqMyma/ZQ+6Wzqe9GDC5AlGZek8l78N2hK1SCnogTQqtI4R
iTtslEtpco329WH3KX4n9vcuoikNvynabja8tlmHgf2vN9PJpbN17oRhOvH64jsNHi2rW8
wZOGBvHx/QcouIhiZ2XiA0PloBrFyQRvbu13RI6CnvO3MW64+Cxaeojwlb4t/KZn58cFS0
u1Pd4CV5JqCMsxfBK5eL5Z1pF2Wgko/oiBP8GELQi0Gz07XYwhADJmaPls6NLA3N6k0Q64
PiNK8JPmx5lnWDndRrL+CHRF9kLLNdbiZXTst9UAG7lYk2m9vfc53yy1+qaCyyhKjcgQAA
AMB9n3Et82hqI39TAEmXak8WC/51tMHkZqAq4BgAXB5Epw34M+bAm60C8gUPDoS3HvjiSC
p6EmIOewTZnVPjXHGptPhlQN6aKqFA3oSBQLgmEW37tMaXnpnATNiBPFclanYkUYOjTM9k
qP75/FWdUu62gjKn1XsyzSQZl/PjB4TkB8fjaWPMtanWdZ64FFnn/yWpq786yoxxrC8qj/
gCRP37uPyWaMDeh4I+rFi2TJZxMdnt8FZInKaniNu04M+RGxgAAADBAPrNvRjcjovM0+WI
nAk9wkX5wfm8u8Bq+aNQiA9R5n2bXbaKJh4OeVAV2E263kQ6KZdaFFmhGU7C8ZM0V/A0ya
f4sUfDNPVMhnxezcIpk+ce8Gyoe/V7iUbo2qyvqhxLuRRhnr3qFpDt79GOkWADNWgIJ8Tf
LQRIUtHiEh+id2AB+sldffzOGEVvcq2YgOeykhMshdBpDzDC5lU+tco02P75Si97qFgVLg
DFi867uLVnf6jaM0fvCSbzI9qyHaWPmQAAAMEA666IwFuXILZhWuYZHeOW8pQvCDWBFxg4
aqEutSW8weOLabRLa/X7U4N2w2w8BlbkiqMbBsf+8lb3VKXTxY93sD14HQZtX87cnGzD2B
7+Et7YswKgaiRrhaRedf6CYX5z9pUww2eP61ilJKciN+OcMv6sPyf8ijFAulT7debgzXqz
H0/kReWEvRX0sdmSsiWl5wgIxeuZ3Zl+4ygSweR3OVZZr+AdArb0LqL84yO0XG86Yq9Sqz
pWCFi/6DJYh9LnAAAAFnNwb29reWJvaUBmNGFiNjVhZTIxYWIBAgME
-----END OPENSSH PRIVATE KEY-----
Then after we change the permission (chmod 600 file_id_rsa), we can try login to the server as spookyboi. but we will prompt for password to use that id_rsa and we do not have the password for this spookyboi user.
There is alternative solution where we can use the SUID binary to cat out the flag3.txt for us because the ouija binary was running as root.
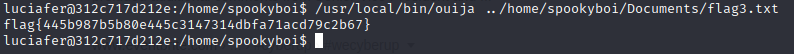
Flag
Flag : flag{445b987b5b80e445c3147314dbfa71acd79c2b67}
talking_to_the_dead_1
Description
We’ve obtained access to a server maintained by spookyboi. There are four flag files that we need you to read and submit (flag1.txt, flag2.txt, etc). Submit the contents of flag1.txt.
ssh hacktober@env.hacktober.io
Password: hacktober-Underdog-Truth-Glimpse
Solution
To solve this challenge, we can navigate to /home/luciafer/Documents/ then we can cat the flag1.txt
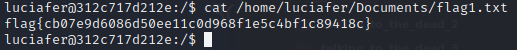
Flag
Flag : flag{cb07e9d6086d50ee11c0d968f1e5c4bf1c89418c}
talking to the dead 4
Description
We suspect spookyboi doesn’t use the root account for this server. There must be some mechanism used to read the flag4.txt file without gaining root. Submit the contents of flag4.txt from the remote machine.
ssh hacktober@env.hacktober.io
Password: hacktober-Underdog-Truth-Glimpse
Problem
Flag
Flag : flag{4781cbffd13df6622565d45e790b4aac2a4054dc}
Hail_Caesar!
Description
This image was found in Ghost Town along with the encoded message below. See if you can decipher the message. Enter the entire decoded message as the flag.
Decode this: TGG KUSJWV QGM
Download Image SHA1: c08156a299a1a2d1ee6c5524a79dafa84e0a700c
Solution
Using ciphey, we can decrypt this caesar encoded message faster.
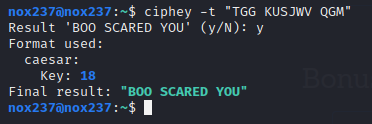
Flag
Flag : flag{BOO SCARED YOU}
Down_the_Wrong_Path
Description
One of our operatives took a photo of a notebook belonging to Donnell. We think it’s a message intended for another member of DEADFACE. Can you decipher the message and tell us who it’s intended for?
Download Image SHA1: 0866977ecb74b039d40886cb5a05a259d28e3773
Hint
Using a search engine, search for “transposition ciphers”
Solution

From the image we will get this encoded string
1
2
3
4
RMTLOBBTERSUXT
EBOLOOOHWGORTA
METSKIUETEFNAC
EREPYATNATOETK
Using tools like https://www.boxentriq.com/code-breaking/columnar-transposition-cipher, we can decrypt this encoded text using bruteforce.
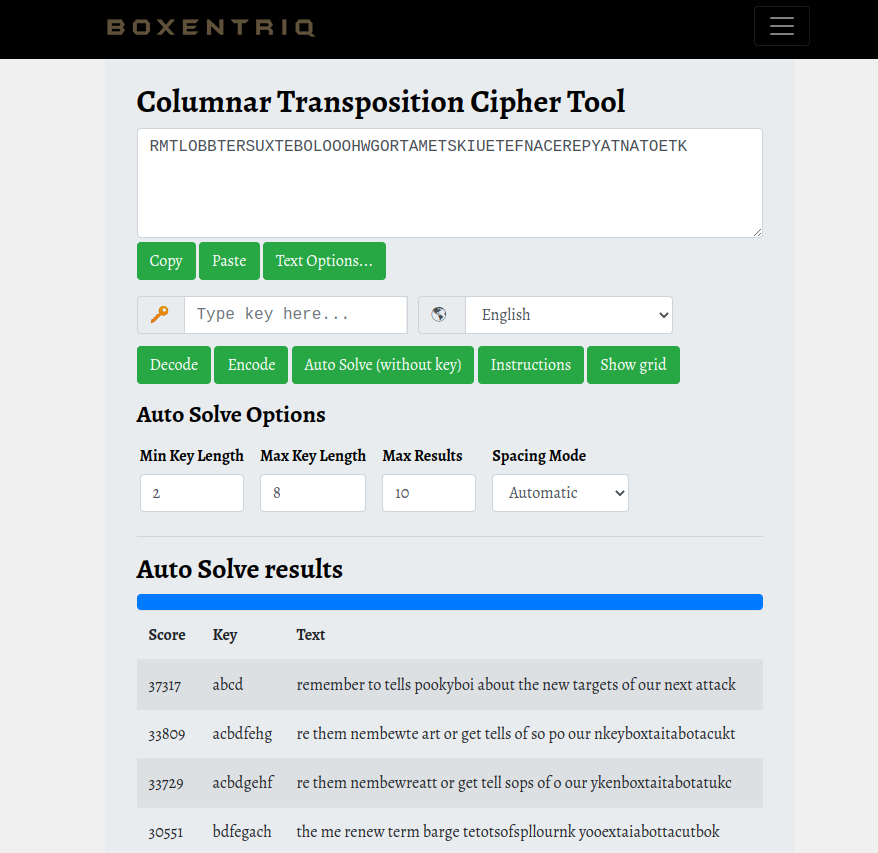
As you can see on the above pictures, we can see the text is “remember to tells pookyboi about the new targets of our next attack”, this message was intented for spookyboi but we didn’t get the ‘s’.
Flag
Flag : flag{spookyboi}
Bone_to_Pick
Description
We intercepted network traffic between two suspected DEADFACE actors. The problem is, we have no idea what we’re looking at. We think it might have critical information. See if you can find the critical information from the link below and submit the flag.
Solution
From the text stirng, it looking like a random text where we difficult to identify this. Here is a small part from the link.
1
_9j_4AAQSkZJRgABAQEAeAB4AAD_4QAiRXhpZgAATU0AKgAAAAgAAQESAAMAAAABAAEAAAAAAAD_2wBDAAIBAQIBAQICAgICAgICAwUDAwMDAwYEBAMFBwYHBwcGBwcICQsJCAgKCAcHCg0KCgsMDAwMBwkODw0MDgsMDAz_2wBDAQICAgMDAwYDAwYMCAcIDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAz_wAARCALQA-ADASIAAhEBAxEB_8QAHwAAAQUBAQEBAQEAAAAAAAAAAAECAwQFBgcICQoL_8QAtRAAAgEDAwIEAwUFBAQAAAF9AQIDAAQRBRIhMUEGE1FhByJxFDKBkaEII0KxwRVS0fAkM2JyggkKFhcYGRolJicoKSo0NTY3ODk6Q0RFRkdISUpTVFVWV1hZWmNkZWZnaGlqc3R1dnd4eXqDhIWGh4iJipKTlJWWl5iZmqKjpKWmp6ipqrKztLW2t7i5usLDxMXGx8jJytLT1NXW19jZ2uHi4-Tl5ufo6erx8vP09fb3-Pn6_8QAHwEAAwEBAQEBAQEBAQAAAAAAAAECAwQFBgcICQoL_
To solve this I insert the string into Cyber Chef, we will get the results that it was a base64 encoded. By decoded it we will get a png file.
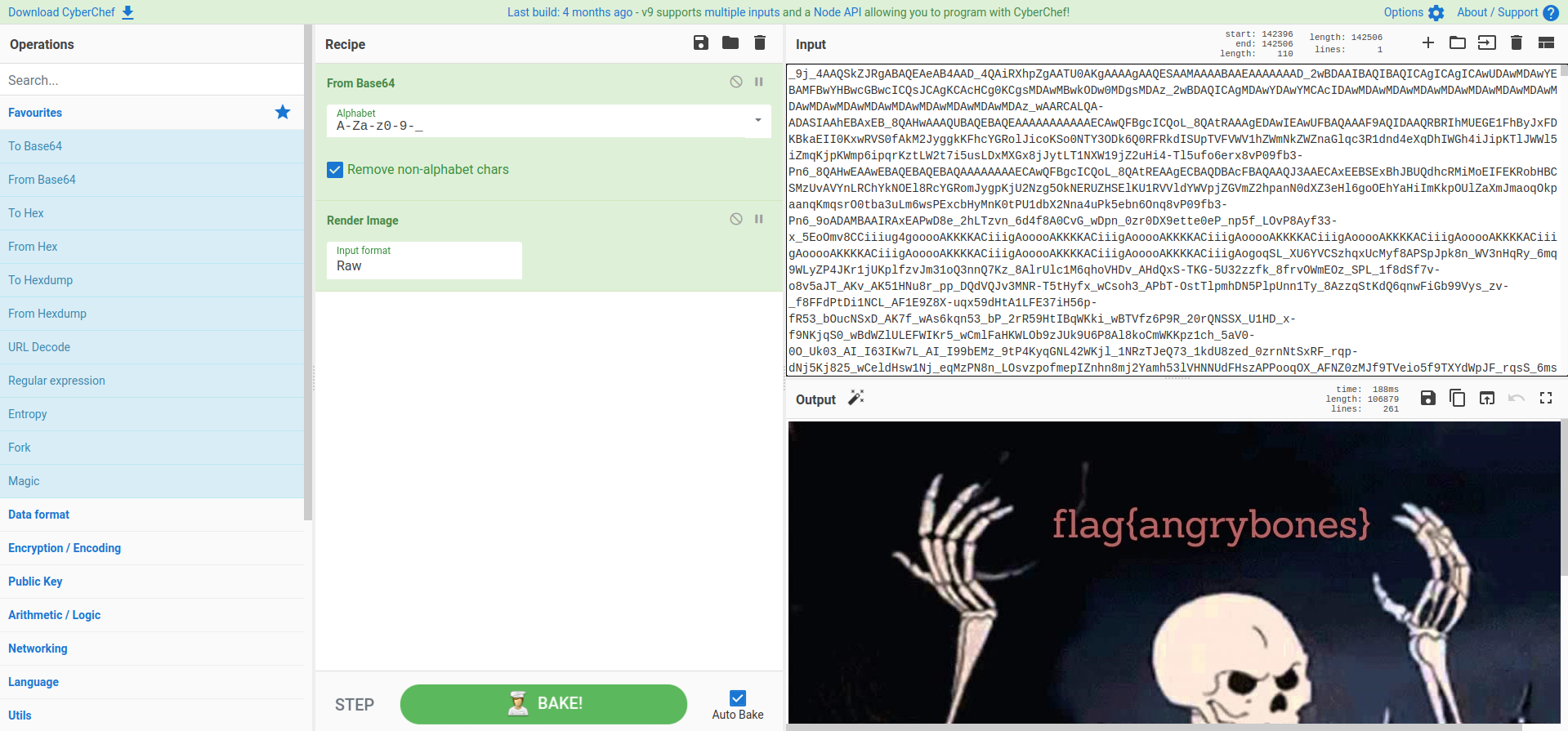
Flag
Flag : flag{angrybones}
Null_and_Void
Description
Using the Shallow Grave SQL dump, which field(s) in the users table accepts NULL values? Submit the field name followed by the single command used to show the information (separated by a comma). Submit the flag as flag{column-name, command}.
Example: flag{employee_id, SELECT}
Use the file from Address Book.
Solution
To solve this challenge, I used query from this link and modified it so we can see the nullable type of the table users.
1
select c.table_name, c.column_name, case c.is_nullable when 'NO' then 'not nullable' when 'YES' then 'is nullable' end as nullable from information_schema.columns c join information_schema.tables t on c.table_schema = t.table_schema and c.table_name = t.table_name where c.table_schema not in ('mysql', 'sys', 'information_schema', 'performance_schema') and t.table_type = 'BASE TABLE' and t.table_schema = 'shallowgraveu' and c.table_name = 'users';
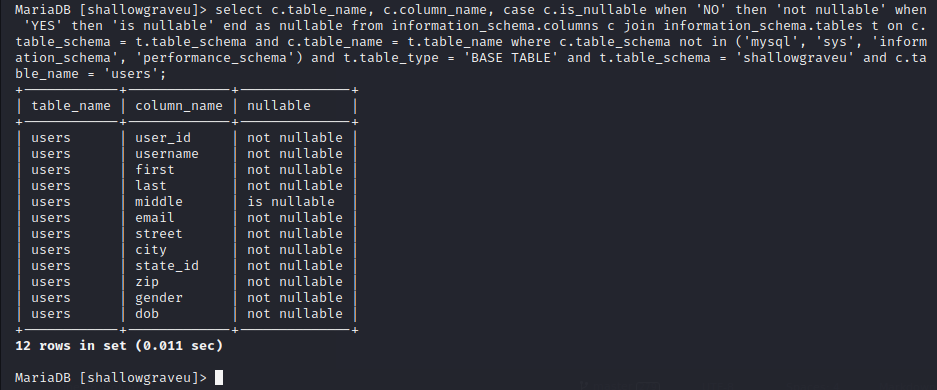
From the query, we can see the results that the middle name can be nullable. After that I cannot submit the flag even after we get the nullable column.
References
Body_Count
Description
How many users exist in the Shallow Grave University database? Submit the flag in the following format: flag{#}
Use the file from Address Book.
Max attempts: 10
Solution
This sql file I imported in from Address Book challenge
To solve this we only need to query COUNT on the mysql.
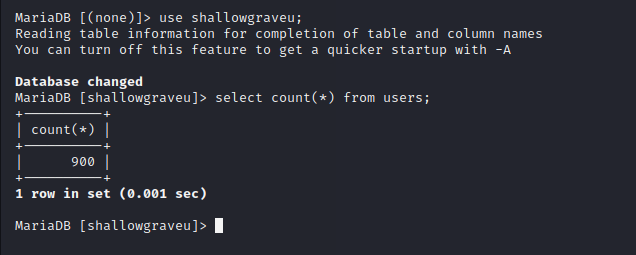
Flag
Flag : flag{900}
Past_Demons
Description
We’ve had a hard time finding anything on spookyboi. But finally, with some search engine finessing, an analyst found an old, vulnerable server spookyboi used to run. We extracted a database, now we need your help finding the password. Submit the password as the flag: flag{password}.
Download file SHA1: 0044305da153df86c49e812ba28532070c7b92ed
Password: hacktober
Solution
After download the data, we will get an out.db file. We can read it using sqlite3.
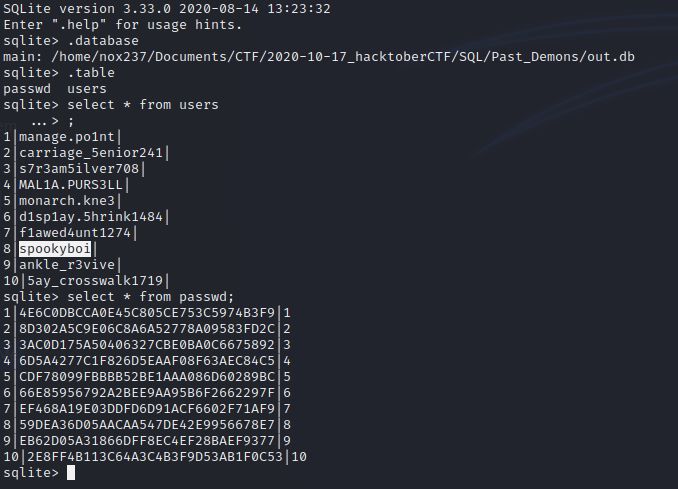
Then after that we can see the challenge highlighted in the description about user “spookyboi”. So we can try to find the password of user spookyboi, but to do that we need to analyze the hash. In this challenge I used https://www.tunnelsup.com/hash-analyzer/.
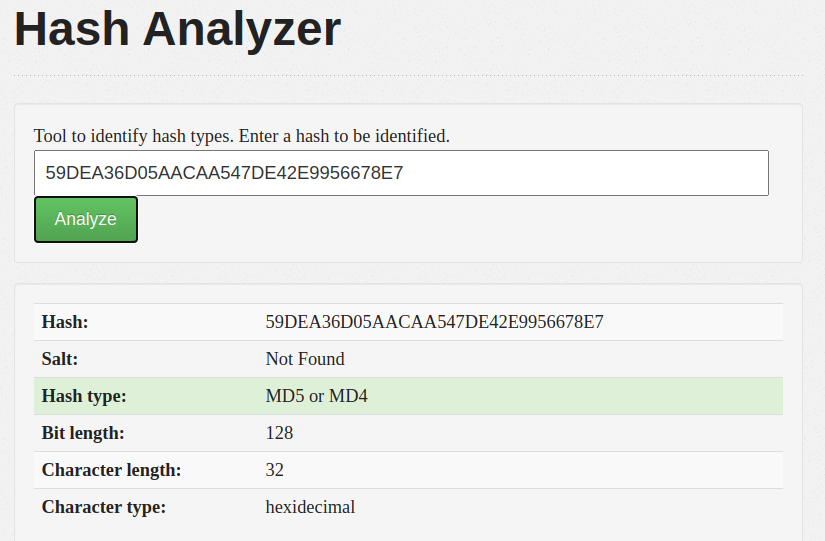
Then after we knew the hash was MD5, we can use tools like crackstation to try get the password.
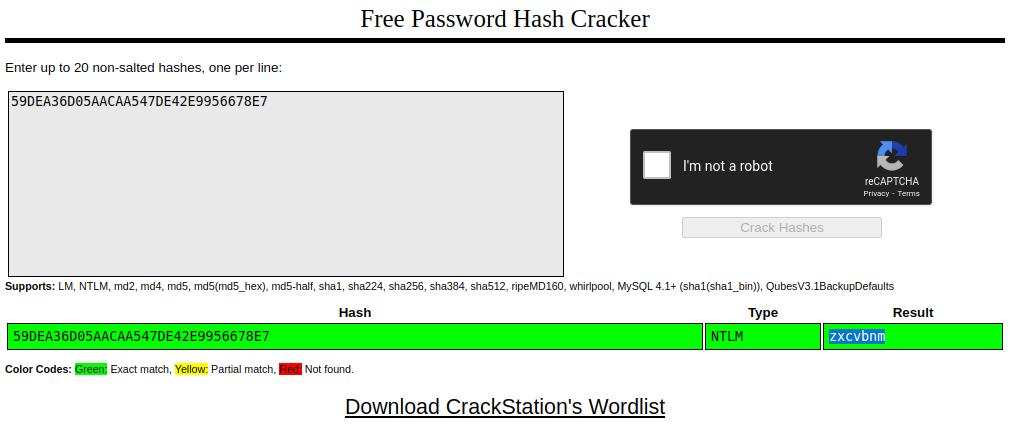
Inserting the password into flag{} format will get us the flag.
Flag
Flag : flag{zxcvbnm}
Calisota
Description
One of our other analysts isn’t familiar with SQL and needs help finding out how many users live in which states. Submit the SQL command used to get the total number of users in the users table who live in California and Minnesota.
NOTE: Send a screenshot of your command and result to syyntax over Slack.
Use the file from Address Book.
Solution
Using the query like this:
1
select count(*) from users u join states s on u.state_id = s.state_id where s.state_full='california' or s.state_full='minnesota';
We will get the the users who live in California and Minnesota.
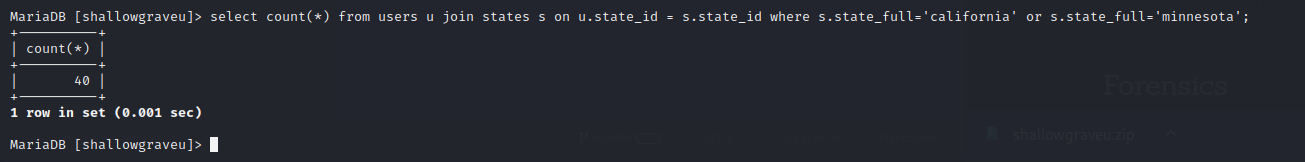
But i not submitting the screenshot to Slack, so i didn’t get the flag.
Address_Book
Description
Shallow Grave University has provided us with a dump of their database. Find luciafer’s email address and submit it as the flag in this format: flag{username@email.com}
Link to File SHA1: 5c2f43259b94c26773e8e7032c81edb65696897c
Password: hacktober
Solution
To solve this, we can load .sql file inside mysql by using command “mysql -u root shallowgraveu < shallowgraveu.sql”. But to do this we need to create the database first. Also when solving this, I have to change the charset to utf8 first and then after that I can insert it to my database.
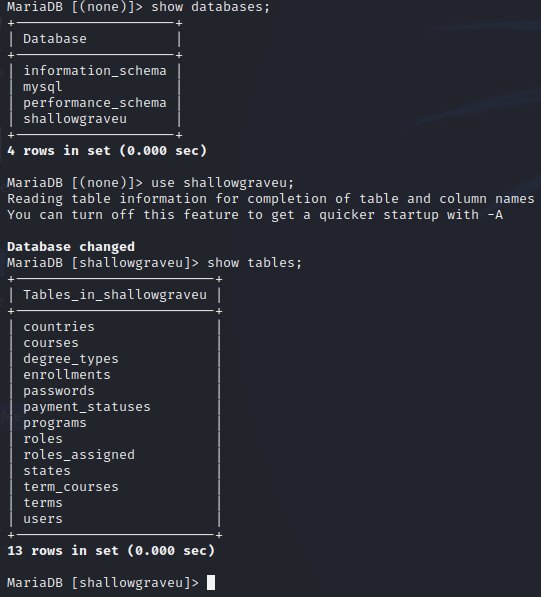
Then if we query to the users table, we will get this output.
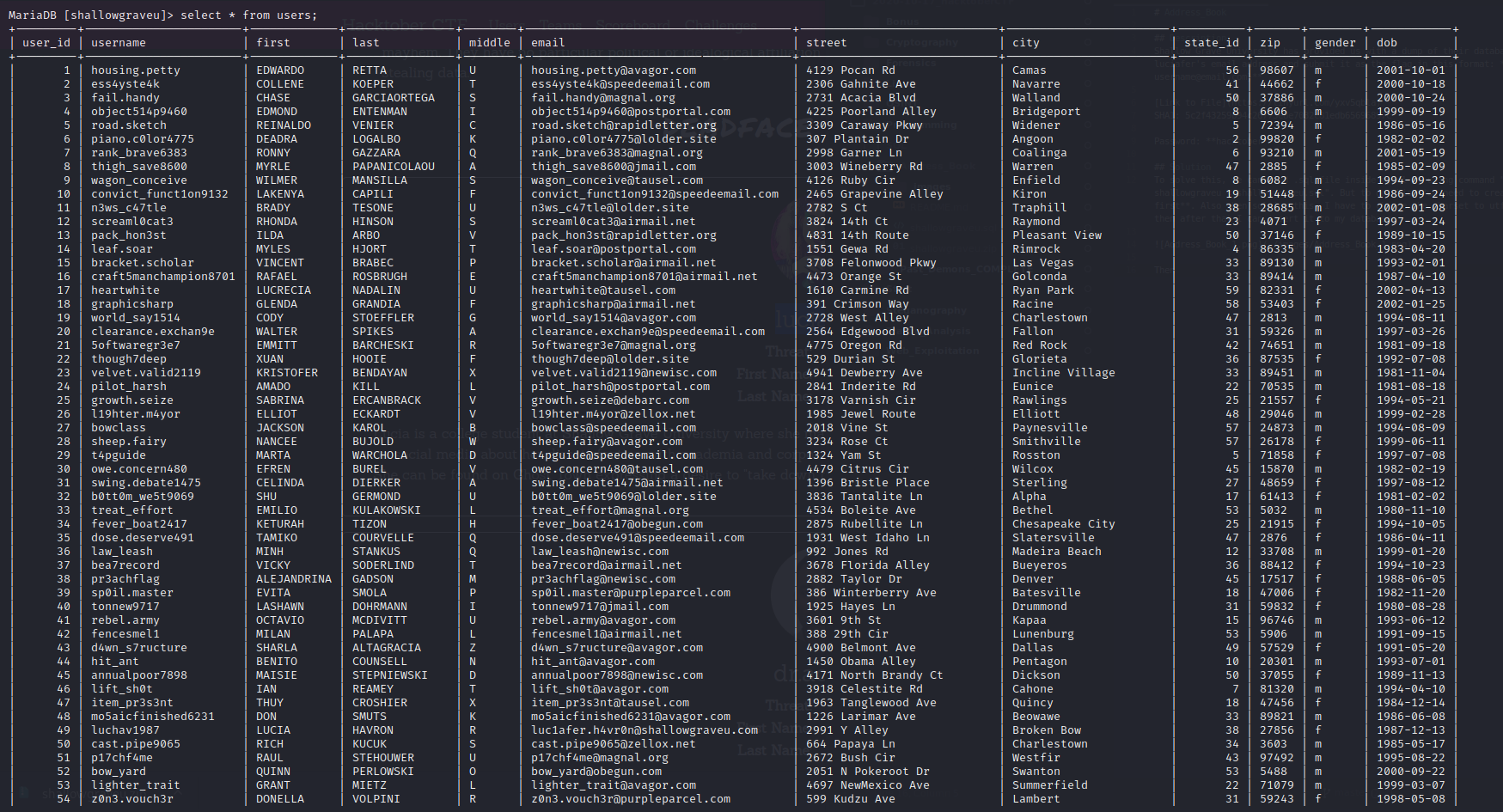
Looking at the intel page, we will see that the luciager first name is Lucia and last name is Havron. Using that information we might be getting the email address.
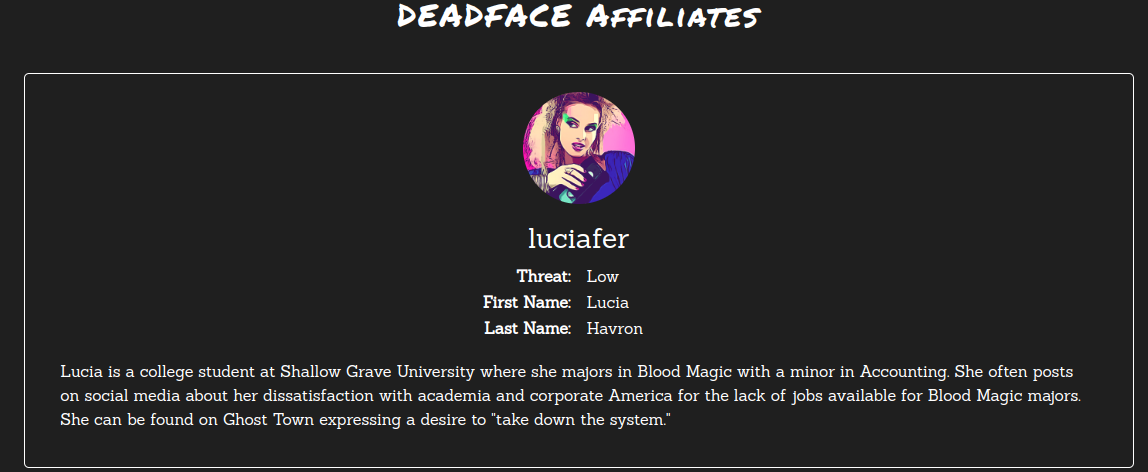
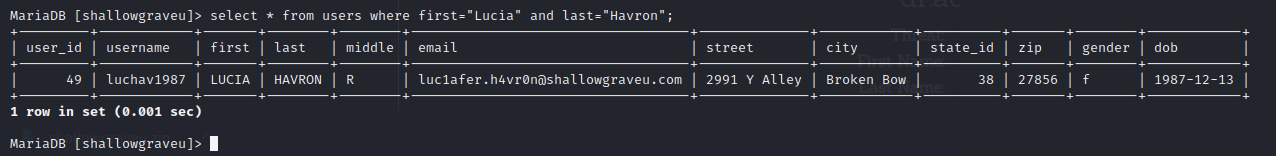
After getting the email, we can insert it into flag{} format and submit it as a flag.
Flag
Flag : flag{luc1afer.h4vr0n@shallowgraveu.com}
Message_in_an_Array
Description
Deadface has left a message in the code. Can you read the code and figure out what it says? You may also copy and paste the code in an emulator. Enter the answer as flag{Word Word Word Word}.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
using System;
using System.Collections.Generic;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
namespace GhostTown
{
class Program
{
static void Main(string[] args)
{
string[] str = new string[4] {"DEADFACE","Nothing", "Stop", "Will"};
Console.WriteLine("{1} {3} {2} {0}", str);
}
}
}
Solution
Based on the code above, the string that will output is “Nothing Will Stop DEADFACE”
Flag
Flag : flag{Nothing Will Stop DEADFACE}